E-MAIL PROTOCOLS: VULNERABILITIES, ATTACKS AND DEFENSE MECHANISMS
Full text
Figure
Related documents
(3) The permission granted by the State Agency in the form of accreditation certificate to the RE Generating Company for the accredited RE Generation Project shall be valid for
• Rizal left Barcelona in the fall of 1882 and established himself in Madrid, the capital of Spain LIFE IN MADRID.. • November 3, 1882- Rizal enrolled in the Universidad Central
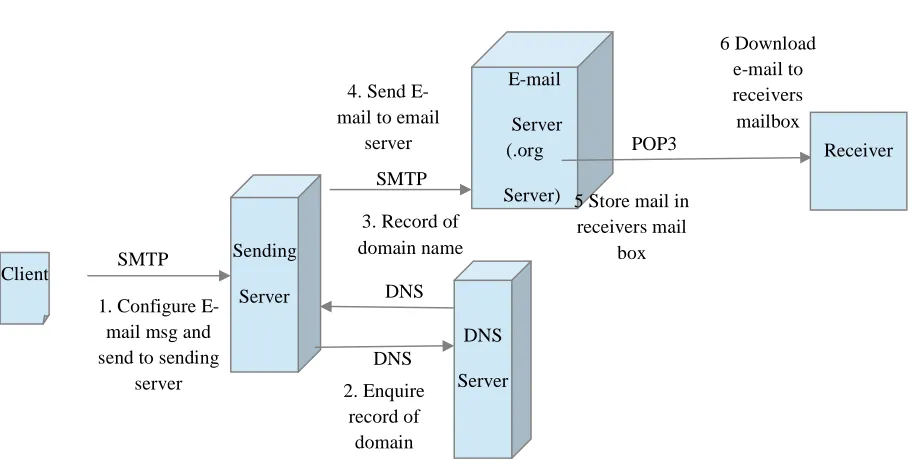
The Simple Mail Transfer Protocol (SMTP), on the other hand, governs the transfer of outbound e-mail from the sending client to the e-mail server (MDA), as well as the transport
A-PDF Mailer uses either your current e-mail client such as Microsoft Outlook, Outlook Express, SMTP (Simple Mail Transfer Protocol) Internet E-mail server!. SMTP is the de
• SMTP protocol between mail servers to send email messages. • client: sending mail server • server: receiving
We apply the proposed methods to discover single nucleotide polymor- phisms (SNPs) associated with type 2 diabetes risk in the WHI Clinical Trial and Observational Study SNP
An Enterprise shall notify all enterprises to which it sends or plans to send encrypted e-mail if it feeds decrypted messages from the Outbound E-mail Gateway to the e-mail
l Like other internet services e-mail is yet another client-server system, called SMTP (simple message transfer protocol).. l You use a mail client program to send a message to