KANYI BYOD Security Framework: For Secure Access and Use of Mobile Devices in a BYOD Environment
Full text
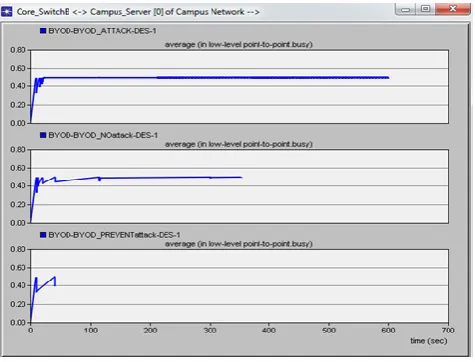
Figure
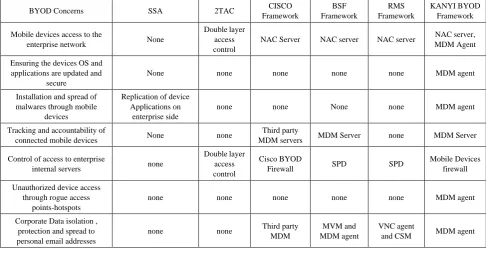
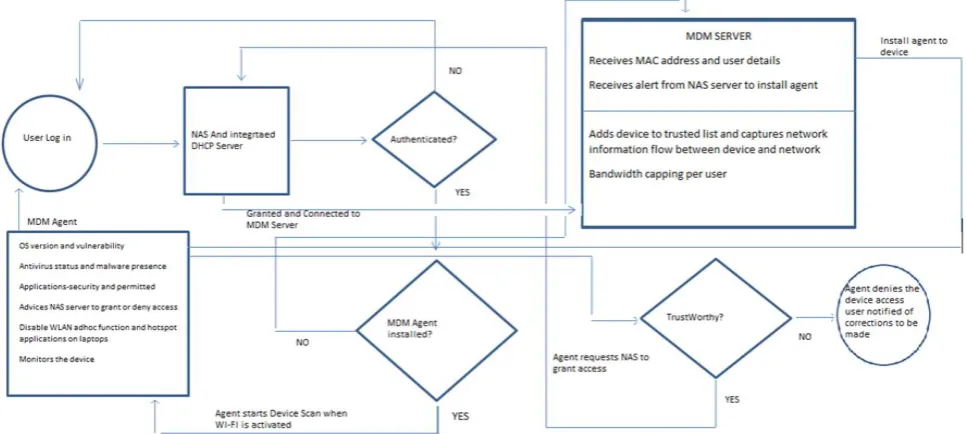
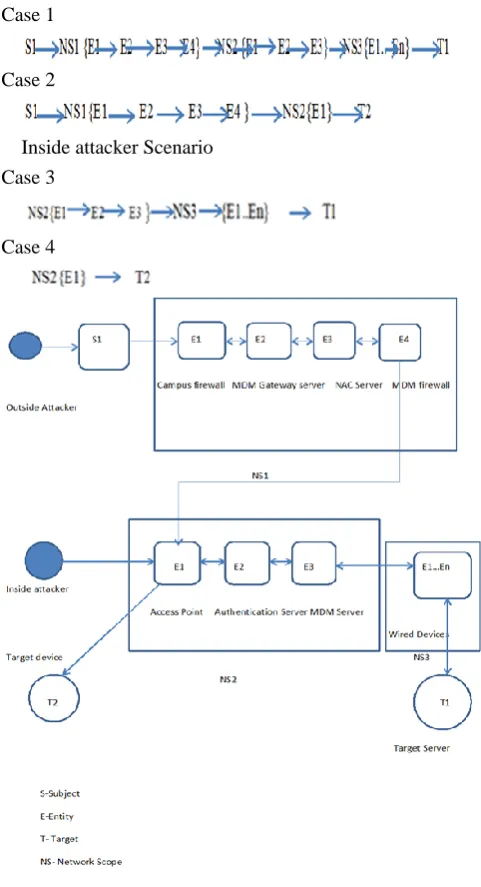
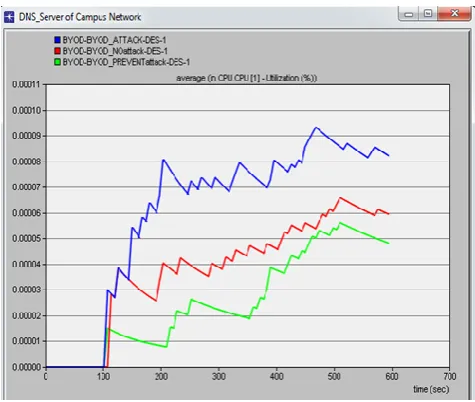
Related documents
За умов комбінованої травми період пізніх проявів травматичної хвороби супроводжується значними порушеннями
Ohio and Montgomery County have similar percentages of late stage diagnoses for all cancer sites reported except cervical cancer and the proportion of late stage cervical
Our reflection on this VDLA exercise demonstrates how the amalgamation of Western and African conceptions of leadership development can identify principles for values
community health aides, emergency medical, itinerant dental and optometry, telemedicine, elder services, and alcohol and mental health services to the Native residents of
The earbuds can be turned on or off individually by holding the Multi-function button on the right earbud, or the Volume down button on the left earbud, until the LED
Production Paperless process execution, WIP tracking, routing control, quality and test data collection / diagnostics. • Interactive Work Instructions & Operator Guidance •
tuberculosis infection promotes adipose tissue in flammation To investigate the involvement of the tissues linked to glucose and lipid metabolism and the progression towards
With these real-time quotes, the specialist on the Chicago Stock Exchange could guarantee to brokers that it would execute a retail market order to buy 500 shares of IBM at a price