5
X
October 2017
Digital security: an Model to work out Overall
Network Security Risk Abuse Stochastic Process
Strategy
V.Ravi Kishore1.K.Vydhei2, Dr.V.Venkata Krishna3 1, 2
Assistant Professor AdityaEngg College 3
Professor & Principal NishitaEngg. College
Abstract: There are numerous security measurements created to protect the pc systems. As a rule, normal security measurements have some expertise in subjective and subjective parts of systems lacking formal connected math models. Inside the blessing study, we tend to propose an arbitrary model to evaluate the threat identified with the system misuse method} process in conjunction with Common Vulnerability rating framework (CVSS) structure. The model we tend to created utilizes have get to chart to speak to the system climate. Using the created demonstrate, one will channel the huge amount of information offered by making a need rundown of defenceless hubs existing inside the system. Once a need list is prepared, arrange executives will make code fix choices. Increasing far reaching comprehension of the risk and need level of each host encourages individuals to execute choices like readiness of security stock and to style arrange topologies.
Catchphrases: Attack Graph, Exploitability, CVSS
I. INTRODUCTION
PC organizes square measure undeniably helpless paying little respect to what level of equipment, programming framework or a blend of every assortment of security parameters square measure consolidated. As long in light of the fact that the system servers offer administrations on totally unique host servers, they rely on the server programming framework that will have security openings that makes them defenseless against vindictive assaults. To discover and additionally thwart the system open assets from suspicious assaults shifted business Intrusion Detection Systems (IDSs) [1]/Prevention Systems square measure available inside the market. This interruption identification/anticipation based for the most part apparatuses gives some sort of a sign that cautions the system head and gives them an incomplete picture of the system [2]. one among one among one in each the first essential difficulties on the present systems is to build up the instrument to blend the danger of all frameworks in a system to judge the general security chance. Keeping in mind the end goal to gage the danger of an outsized scale venture, relate degree director ought to examine not exclusively single defenselessness abuse however moreover the multi-organize and furthermore the multi-have powerlessness assault used by the aggressors. to incorporate this reality, relate degee assault diagram is developed to search out the consistent connection between different endeavors. Be that as it may, once size and intricacy of the system will build, 2 noteworthy issues happen. Initially, the assault diagram develops exponentially once the size of the system and algorithmic manage many-sided quality increment. Besides, fathoming the learning sent by the diagram winds up noticeably troublesome. In this way, the assault chart that tends to the issues specified before were picked and that we can put forth a defense for any inside the following area.
Almost no has been exhausted logical and investigation group to create connected science display that measure the general system security hazard. The vast majority of the work concentrates on subjective and subjective side of systems while not having formal factual model. to encourage forestall this disadvantage, we tend to present the connected science display that utilizations Markov chains in conjunction with CVSS system measurements to explore dangers identified with structures of grouped systems. The model might be utilized to recognize pivotal hubs inside the host get to chart wherever assailants could likewise be well on the way to center. bolstered that information, a system overseer will make fitting, organized determinations for framework settle. Further, an adaptable hazard positioning method is outline, wherever the choices made by relate miscreant might be balanced utilizing an inclination issue. The model might be summed up to be utilized with modern system conditions.
II. FOUNDATION AND TERMINOLOGIES OF CYBER SECURITY
goal. Figure one gives the schematic introduction of the CVSS system, [5] and strikingly uncovers the all encompassing arrangement to figure the base score adjacent to Exploitability sub score and Impact sub-score.
A. Vulnerabilities
Weakness might be an imperfection that exists in pc assets or administration which will be misused by one or a ton of dangers. A bundle defencelessness [6] is Associate in Nursing occasion of a slip inside the determination, improvement, or design of bundle such its execution will abuse the security strategy. Assailants unremarkably utilize the far-celebrated around the world vulnerabilities that territory unit recorded openly on National Vulnerability data (NVD) [7] to enter the framework. Regularly assailants could utilize a helplessness that has not been revealed out in the open that is named zero day defencelessness. Zero day weakness stays obscure to merchants; hence information with respect to the new vulnerabilities gives the assailants a free go to assault any objective host. The zero day assault has not been utilized in this investigation.
B. Assault Graphs
[image:3.612.76.534.313.533.2]Aggressors in some cases infiltrate any style of electronic system by means of an arrangement of adventures where each endeavor inside the chain makes the dream for future adventures. A blend of such endeavors manufactures the chain known as assault way; an arrangement of such assault strategies build up the assault chart. AN assault diagram could be a reduced outline of all strategies through a framework that closures in amid AN exceedingly in an exceptionally state wherever a participant has effectively accomplished its objective [9] [10]. There are a few calculations that are created inside the logical and examination group to build the assault charts. In any case, it's appallingly hard to investigate the system by means of assault
Figure 1.Regular helplessness framework for base metric figuring model.
Chart once assortment of hubs and many-sided quality of the system increment. As the versatility and unpredictability of the system increment exponentially, the calculation cost to frame the assault chart will increment. Subsequently, it's hard to translate the assault diagram precisely. On the inverse hand, the greater part of the assault diagrams square measure intended for one target, and can't be wont to esteem the general security of the systems with many targets.
C. Normal Vulnerability grouping framework (CVSS)
III. DIGITAL SECURITY ANALYTICAL FRAMEWORK
[image:4.612.83.534.163.356.2]The model given beneath in Figure 2, demonstrates a superior clarifies the digital security display. For effortlessness confined quantities of hubs are blessing in our system .However, on the grounds that the size and multifaceted nature of the system increment, we will utilize any very assault diagram era apparatuses [19] to assemble the mean assault chart of intrigue. Hubs blessing on the assault chart speak to the individual host. Each host runs very surprising assortments of administrations and there could exist fluctuated vulnerabilities. CVSS appoints
Figure 2.Digital security expository system.
IV. SHOW REPRESENTATION
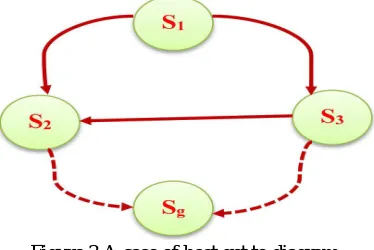
The focal component of the anticipated irregular model exclusively relies upon the host get to chart said inside the past area. Before diving into the demonstrating approach, enable us to formally present a defense for the host get to diagram as appeared underneath by Fig 3 In Figure three beneath, I , 1, 2,3, , S I = g square measure have hubs and g S might be an objective hub. A hub speaks to a pack inside the host get to chart; thus, the amount of hubs is equivalent to the amount of hosts inside the system. Also, coordinated edges between two hubs speak to the entrance connection between the comparing 2 has all together that there's just 1 guided edge from one hub to an alternate and no more. Consequently, there are no numerous edges inside the diagram, and our anticipated model holds just the absolute best access accomplished between the hosts, since more elevated amounts of access to the goal have implies that extra capable assaults square measure accomplished. A coordinated strong edge lines from have one S to have two S in Figure three speaks to the entrance accessible on two s from one s. Essentially, broken lines from have two S to have g S delineate that there square measure elective middle of the road hubs blessing in the middle of these hubs and a similar defence is pertinent to elective hosts.
Figure 3.A case of host get to diagram.
V. THE RISK BOLSTERED RANKING
[image:4.612.213.400.555.680.2]worth is processed upheld the amount of hosts blessing inside the host to diagram. Assume there exist N hubs inside the host get to diagram; at that point only set all the hub positions equivalent to 1/N. first this essential hazard is first infused by the starting hub of partner degree attacker.
[image:5.612.82.533.157.560.2]This hazard worth streams level by level till merging. the entire hazard positioning calculation is spoken to by the schematic outline given below
Figure 4.Flow chart to compute risk of overall network.
Figure 5. Experimental topology.
VI. CONCLUSION
In this examination, we've built up an irregular model for cybersecurityabuse have get to chart to see the general system security chance. Our model uses Markov chains in conjunction with CVSS system to comprehend and examine the hazard identified with the structure of the system. This created display decides the basic hubs existing inside the host get to assault chart wherever the assailant is apparently to go to. bolstered this information, a system manager can make the worthy call in regards to framework repair with needs.
REFERENCES
[1] Jha, S., Sheyner, O. and Wing, J.M. (2002) Minimization and Reliability Analyses ofAttack Graphs (No. CMU-CS-02-109). Technical Report, School of Computer Science Carnegie-Mellon University, Pittsburgh.
[3] Rajasooriya, S.M., Tsokos, C.P. and Kaluarachchi, P.K. (2016) Stochastic Modellingof Vulnerability Life Cycle and Security Risk Evaluation. Journal of InformationSecurity , 7, 269-279. https://doi.org/10.4236/jis.2016.74022
[4] Kaluarachchi, P.K., Tsokos, C.P. and Rajasooriya, S.M. (2016) Cybersecurity: A Statistical Predictive Model for the Expected Path Length. Journal of Information Security, 7, 112-128. https://doi.org/10.4236/jis.2016.73008
[5] Mell, P., Scarfone, K. and Romanosky, S. (2007) A Complete Guide to the CommonVulnerability Scoring System Version 2.0. FIRST-Forum of Incident Response andSecurity Teams, 1-23. https://www.first.org/cvss/cvss-v2-guide.pdf
[6] Krsul, I.V. (1998) Software Vulnerability Analysis. Doctoral Dissertation, PurudeUniversity, Indiana. [7] National Vulnerability Database (NVD). https://nvd.nist.gov/
[8] Bilge, L. and Dumitras, T. (2012) Before We Knew It: An Empirical Study of Zero-Day Attacks in the Real World. Proceedings of the 2012 ACM Conference onComputer and Communications Security, Raleigh, 16-18 October 2012, 833-844.https://doi.org/10.1145/2382196.2382284
[9] Jha, S., Sheyner, O. and Wing, J. (2002) Two Formal Analyses of Attack Graphs.Proceedings of 15th IEEE Computer Security Foundations Workshop, Cape Breton,24-26 June 2002, 49-63. https://doi.org/10.1109/CSFW.2002.1021806