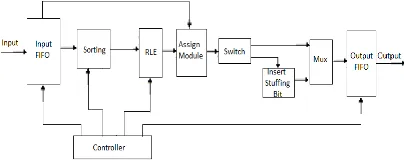
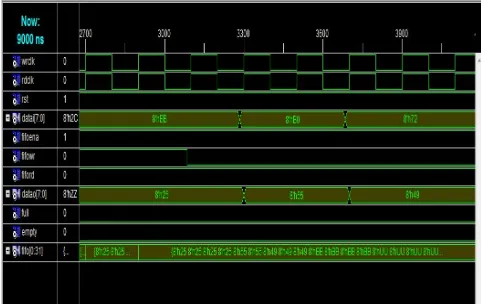
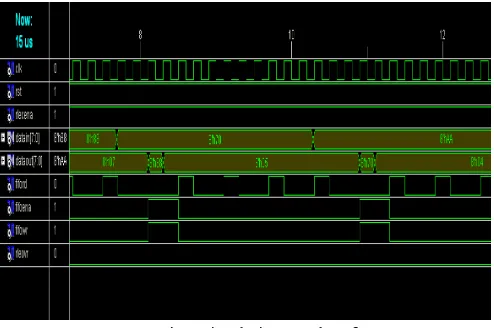
Modified Huffman Coding Technique for High Secured Data Transmission
Full text
Figure

Related documents
World Health Organization and the European research Organization on Genital Infection and Neoplasia in the year 2000 mentioned that HPV testing showed
2 ] 2+ unit reveal no unusual features. Virtually the same distances are seen in the acetato-bridged complex 4 [67]. A large number of metal complexes containing
Experiments were designed with different ecological conditions like prey density, volume of water, container shape, presence of vegetation, predator density and time of
In theory, FRET is a radiationless energy transfer process, so ideally, a single emission spectrum of the output fluorophore should be observed, as illustrated in Fig.2.7
The theoretical concerns that should be addressed so that the proposed inter-mated breeding program can be effectively used are as follows: (1) the minimum sam- ple size that
Since HPAI outbreak occurred in Asian and European countries, the African continent had been encountering great threat of the epidemic outbreak. Unfortunately, HPAI took place
Thus, a training set of the 16 synthesized compounds were used in this study to construct a pharmacophore model using hydrogen bond acceptor, hydrogen bond
Sponsor may author one "Guest Blog" on MBA Veterans Blog Reserved table at Breakfast and Lunch to connect with attendees Complimentary job posting on MBA Veterans Connect