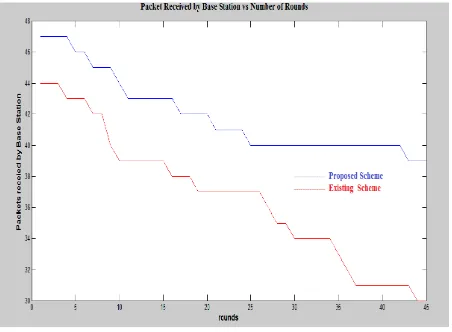
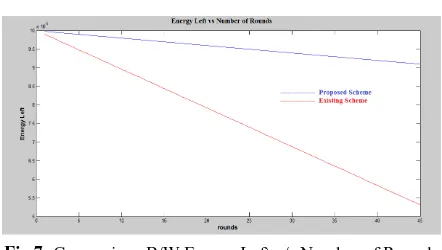
Selective Forwarding based Intrusion Detection System for Secure Wireless Sensor Network
Full text
Figure



Related documents
This qualitative study was designed to collect detailed information about the different approaches of secondary-level visual-arts teachers in Northern California who have
Si bien es necesario reconocer que las medicio- nes de la pobreza basadas en indicadores moneta- rios brindan una mira parcial de un fen´ omeno que es multidimensional, no
need for previous skills. Although few studies have been done on the application of heat and cold on labor, its effect was examined on other clinical conditions.
During high speed, engine desires to have early opening of intake valve, thereby increasing the valve overlap with exhaust valve to reduce pumping losses.. Also,
Enterprise Architecture is used to describe an entire organization – using both business and technical views. “The enterprise architecture is the organizing logic for a firm’s
As marketing can help to realize new opportunities for forestry, the aim of this research study is to shed more light on how forestry enterprises in Slovakia use marketing tools
Led by a CFR scholar and/or religious community leader, the monthly CFR Religion and Foreign Policy Conference Call series gives religious and congregational leaders and
In Personalized collaborative environment webDAV assists the intelligent agent tutor to interact with the web servers to collect and produce cognizant knowledge to to the