Unified Threat Management
Full text
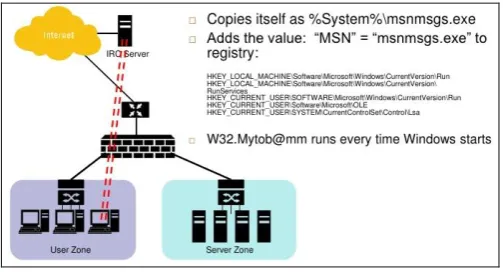
Figure


Related documents
Thus, through the literature review, a conceptual model was proposed and an empirical research was carried out, taking into account the following main objectives: to contribute
The research identified policy consistency (a.k.a. “visibility”), financial stability, and global trade issues including insufficient protections for intellectual property,
Based on the full car model and the semi-active suspension constraints detailed in previous sections, the control problem we are interested in solving in this work is the
We also use data from the U.S. NRC’s Power Reactor Status Reports. These
Chapter 7, QFit – Basic Mode – Fitting window – Buttons, memory tabs and compare
DP = Direct, Spring-to-Open, Valve Locked in Closed Position (Lock at pressure end of stroke. Includes MO plus chain) RP = Reverse, Spring-to-Close, Valve Locked
That index does not cover the LAST_NAME column—the INDEX RANGE SCAN can consider the SUBSIDIARY_ID filter only; the Oracle database shows this in the “Predicate
Reservists using privately owned or government owned equipment must sign an agreement out- lining the required equipment, software, hardware, data, and telecommunication