SQL Injection Attack : Detection and Prevention
Full text
Figure

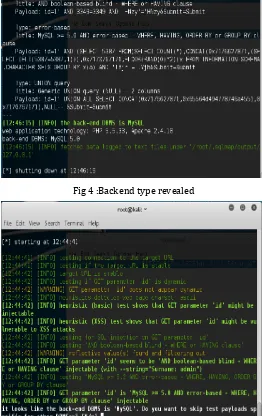

Related documents
Introduction: The aim of this study was to investigate if defective repair of DNA double-strand break (DSB) in head and neck squamous cell carcinoma (HNSCC) could be used as an
“Man, then, as he changes place and society, nds himself in a position of discovery or understanding at ever greater depths, all of which he has in common with other men,
In this chapter, I shift from thinking about habit in relation to mid-century literary allusion and textuality to analyzing the relationship between Wilkie Collins’s unconscious
There were differences by top source country with 94 per cent of Essential Skills workers from India gaining residence as a principal skilled migrant compared with 89 per cent
But also the training of model can be a problematic task: even if it can be easily performed in an ATC system (the ATC systems have a testing environment that is a copy of the
These findings complement results from the RAND Health Insurance Experiment, a large experimental study of health care costs and utilization conducted from 1971 to 1986, to improve
In both cases, resting state FDG-PET, fMRI, and EEG showed a functionally preserved right hemisphere, while DTI showed underlying differences in structural connectivity highlighting
% Script to calculate the specific area under a Gaussian probability % density function using the Rectangular Rule?. w=0.1; % This is the width of