Efficient Data Storage Security in Cloud Computing
Full text
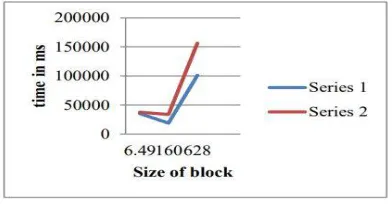
Figure


Related documents
The first task which must be taken into account in determining the antonym in Albanian, is not the negative, but opposite character of the meanings of words and stable compound
Keywords: Exclusive breastfeeding, Infant feeding practice, infant formula feeding, HIV-infected peripartum women, South Africa, WHO guideline.. *
Table 6.2 Estimates of background and source location and intensity parameters ob- tained from the mean values of the DRAM chains constructed with a narrow prior on the
Yet, in Tesla transformer the parasitic capacitances, self and mutual inductances, resistances of the coils (due to their dimensions, separation between turns, and diameters of
There is no immediate proof on the relationship between maternal pre-pregnancy BMI or GWG and the perinatal results of GDM moms, and stays hazy whether the
The finest fractions of the particles expected to be present in the washwater after collection by the street sweeping machine were in the same size range as those found in the
Abstract Growth characteristics [stem diameter ( D ), tree height ( H ), and bole volume ( V )], stress-wave velocity (SWV), and Pilodyn penetration ( P ) were measured for 21