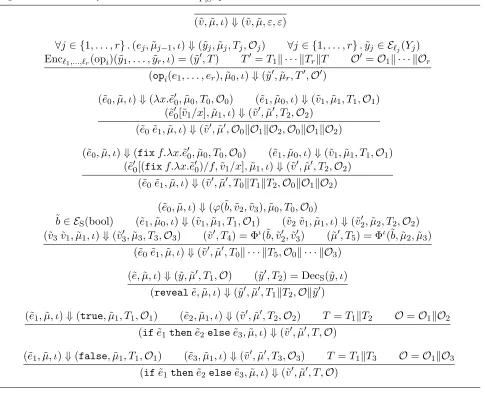
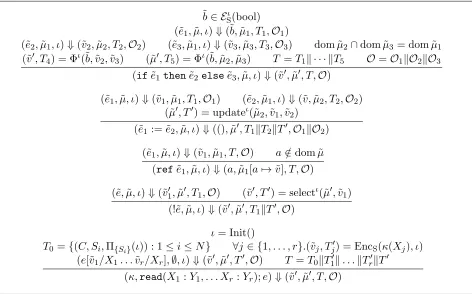
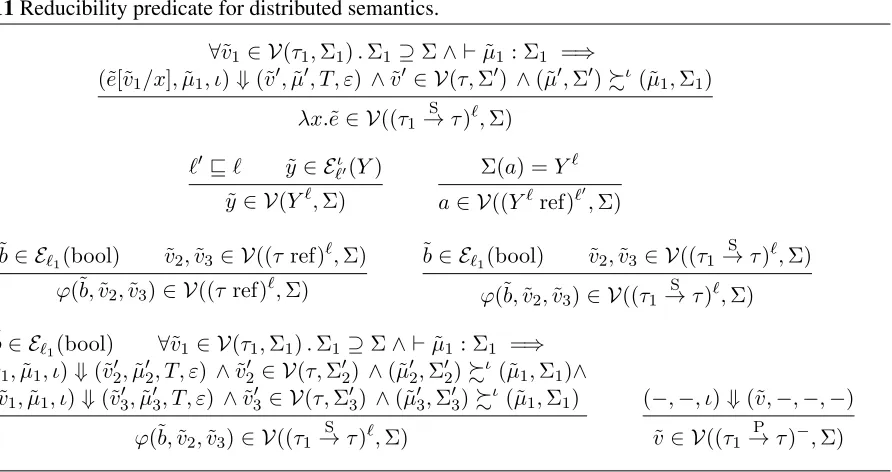
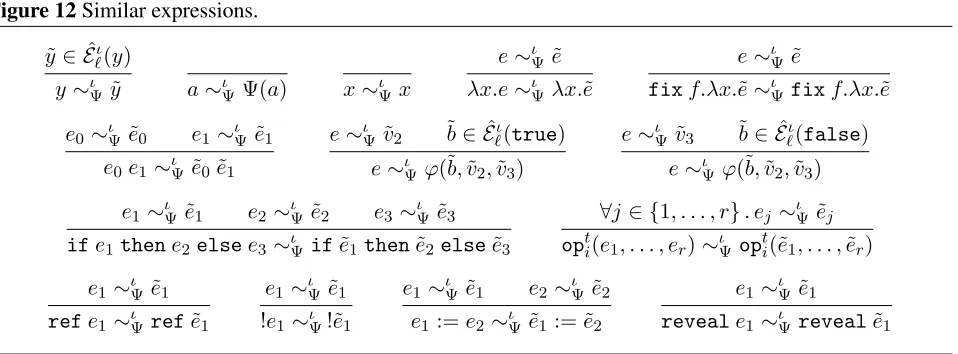
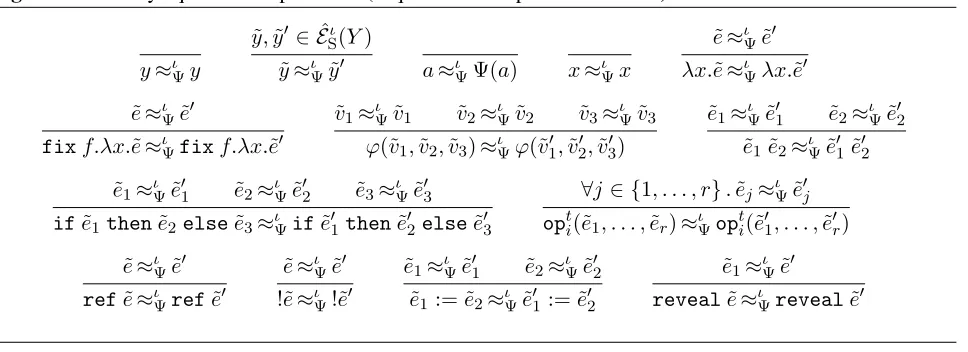
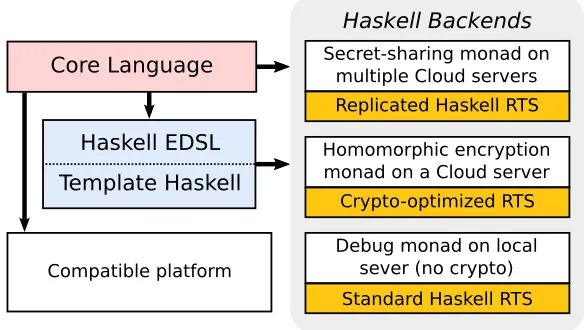
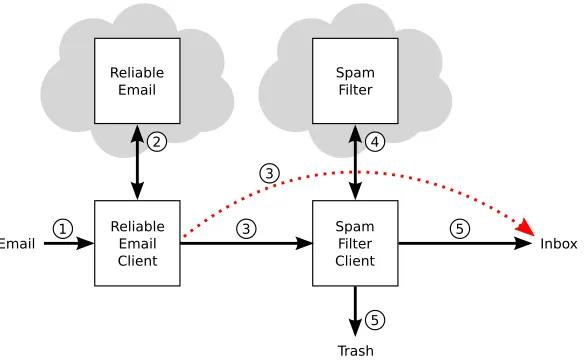
Information-flow control for programming on encrypted data
Full text
Figure


Related documents
The team from Mayo Clinic in Scottsdale compared robotic-assisted surgery, laparoscopic surgery and open laparotomy in patients undergoing radical abdominal hysterectomy with
prehospital through the ED to the time of ward admission, combined with an elevated ED lactate identifies patients with suspicion of sepsis at highest risk of in-hospital
T HE D EVELOPMENT OF THE A LARM S ECURITY I NDUSTRY IN THE U NITED S TATES
Our Homelessness Project continues to work in partnership with Dumfries and Galloway Council’s Homeless Department as well as other external agencies within the area to
With the continued increase of participation at youth, high school, and collegiate levels (National Collegiate Athletic Association 2015; National Federation of High Schools 2015;
Today locality is the result of using information and communication technologies in all departments of our life, but in future all cities must to use smart systems for improve
On average, there is a substantial achievement gap between first-generation immigrant students and their second and third generation peers, but the effect of first-generation
The value of “Alice announces a pure strategy” is 3 (Alice will pick the second row, which is everywhere better for Alice than the first row), and the value of “Betty announces a