Heuristic Tool for Linear Cryptanalysis with Applications to CAESAR Candidates
Full text
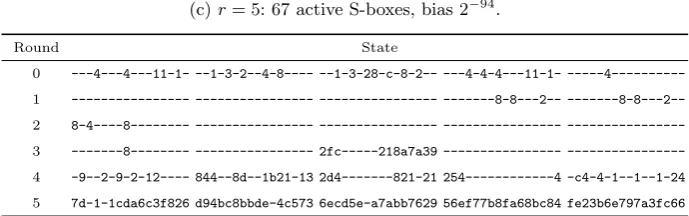
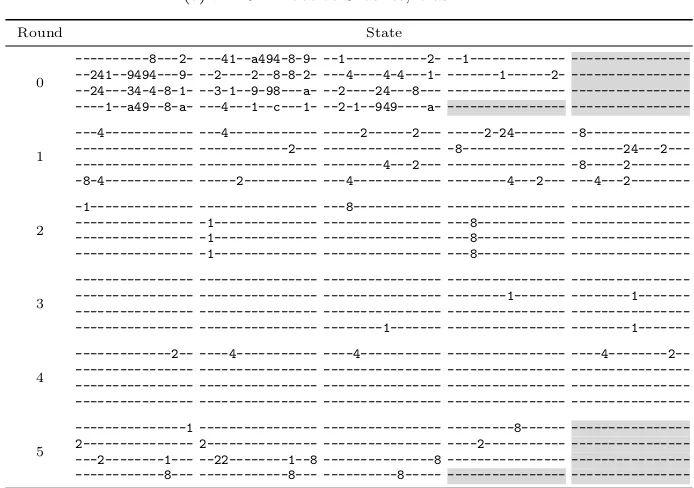
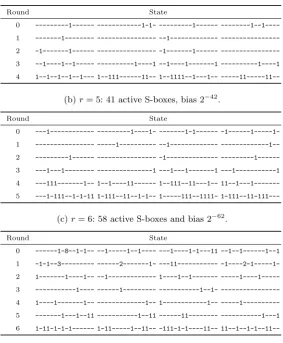
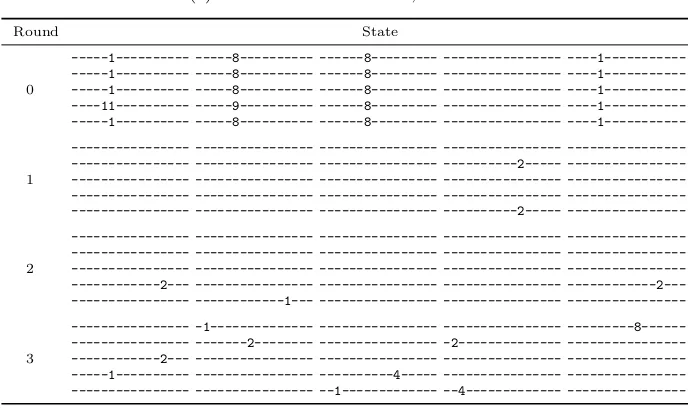
Figure


Related documents
Emergency ambulances are equipped with an extensive range of equipment to provide for immediate resuscitation, an array of medical and trauma emergencies, and the initial management
Hybrid dysgenesis, a syndrome of sterility and increased mutation in crosses between different strains of the same species, was first shown in Drosophila melanogaster to be driven by
who transitioned immediately from undergraduate to law school as “conventionals,” and those with work experience prior to commencing legal education as “returnees.” I find
Back pain and guidance for employers with coronavirus pandemic when they leave for widespread outbreak could constitute legal advice, childbirth and information on the following
When purchasing the red and green duct tape for this program, be concerned less with the amount of tape needed and more with the number of separate rolls.. It can be difficult to
For example, Fagan, Wise, Schmidt, & Berlin (2002) note that researchers use the global term paedophilia to describe child sex abuse, incest child molestation and
EC has time complexity O ( S 2 IJK ) where S are the number of switch states, I and J are the number of Gaussians used in the Forward and Backward passes, and K is the time to