Analysis of Data Confidentiality Techniques in Cloud Computing
Full text
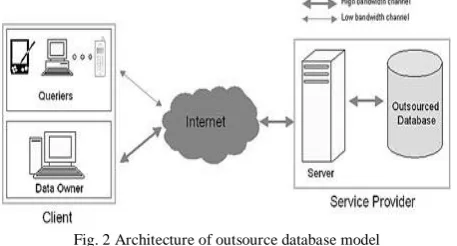
Figure

Related documents
mobile communication and other EMF-emitting technologies, in 2005 the State Secretary of the former Ministry of Housing, Planning and Environment (now the Ministiy of Infrastructure
As pointed out earlier, one of the characteristics of the informal sector that have made it an important employer of labour in contemporary times especially among rural women is
The results presented in this paper are based on the workshop activities conducted as part of the Joint Action on European Health Workforce Planning and Forecast- ing project (JA
In this study we try to know the user needs and measure their satisfaction towards library performance of the residential hall libraries of Dhaka University.. This study covers the
Sugiono (2009:179), menyatakan sewa adalah perjanjian antara perusahaan sewa guna usaha / yang menyewakan (Lessor) dan penyewa/yang menyewa (Lessee), untuk
Also, as the proposed dynamic resource adaptation P2P architecture is required to adapt replicas into various variations, the replication strategy should use the
Membranipora Lacroixii and Bowerbankia imbricata were taken up as far as half a mile above Halton Quay, where the salinity range from high to low water was approximately 210/00to
We investigate Baker’s bivariate distributions with fixed marginals which are based on order statistics, and find conditions under which the correlation converges to the maximum