Generic, Secure and Modular (GSM) Methodology for Design and Implementation of Secure Mobile Applications
Full text
Figure

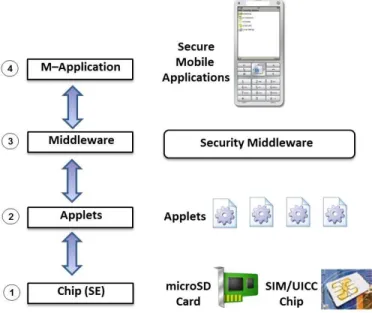


Related documents
Production and business areas Organisational structure Corporate governance Board of directors Board of statutory auditors Risk Management.. Internal audit and internal control
[r]
Style 744 FireLock flange adapters provide rigid joints when used on pipe with standard cut or roll groove dimensions and consequently allow no linear or angular movement at the
pricing basis, then the addition of surrenders has little impact on profitability. n A more generous surrender value basis would
“Ballyhoo Magazine, Parody, and the Visual Rhetoric of Early Twentieth Century Consumer Critique.” presented at the National Communication Association Conference in Chicago,
At a time when markets are constantly fluctuating, organizations need to frequently revisit their strategies, operations and portfolio of offerings to reach a competitive
Of the Hicksian cross-price elasticities between the different energy categories on the one hand and the composite good, non-energy consumption, on the other, one is
The study found positive perceptions of higher education and K-12 personnel that work with Confucius Institutes regarding adherence to principles of academic freedom, adherence to