SECURING DNS USING ECC
Full text
Figure



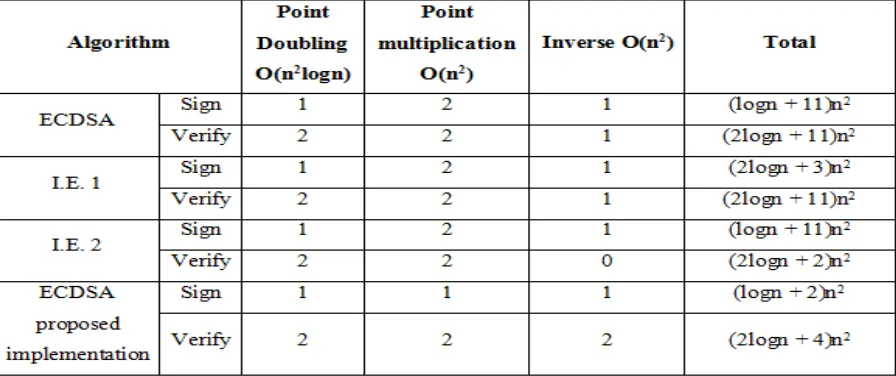
Related documents
Each applicant seeking admission into the Nuclear Medicine Technology program will be required to visit a local hospital nuclear department to observe its operation for a minimum of
Our PFs and MAs who answer phones and schedule our patients, use a triage book to determine how soon a patient needs to be seen.. Another example out of our 99-page triage book
Application Layer 2-18 requesting host cis.poly.edu gaia.cs.umass.edu root DNS server local DNS server dns.poly.edu 1 2 3 4 5 6 authoritative DNS server dns.cs.umass.edu 7 8
• Iterative queries: When the name server of a host cannot resolve a query, it sends a referral to another server to the resolver.
7 The fact that certain prophetic activities display an unmistakably shamanistic strain, such as magic, miracles, spirit possession and ecstasy, cannot be denied,.. and,
The gradual removal of regulatory barriers allowed the CECA, in periods of strong growth of the Spanish economy, to offer their associates access to shared resources including
requesting host cis.poly.edu root DNS server local DNS server dns.poly.edu 1 2 4 5 6 authoritative DNS server dns.cs.umass.edu 7 8 TLD DNS server 3 Recursive queries recursive query:.
–One place where all mappings are stored –All queries go to the central server. • Many