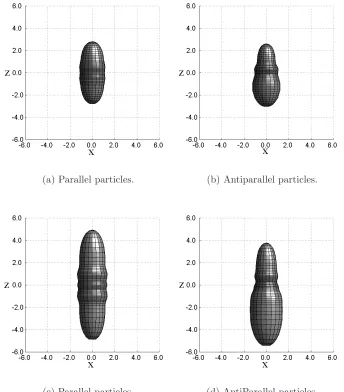
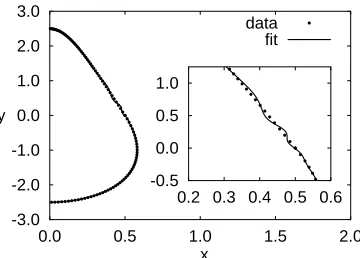
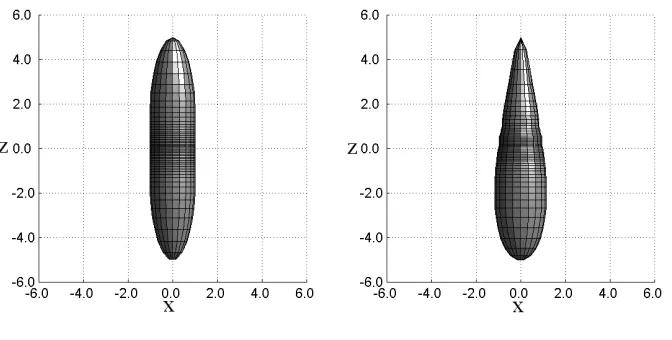
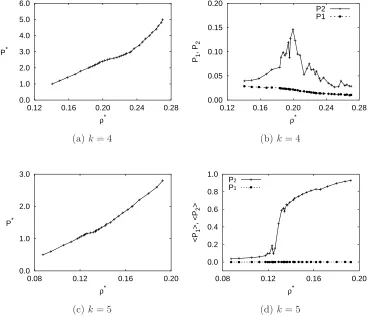
Computer simulations of hard pear shaped particles
Full text
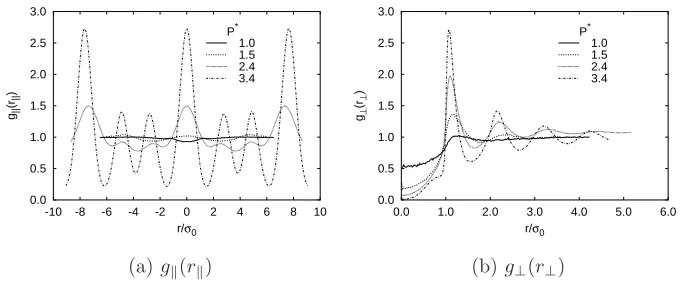
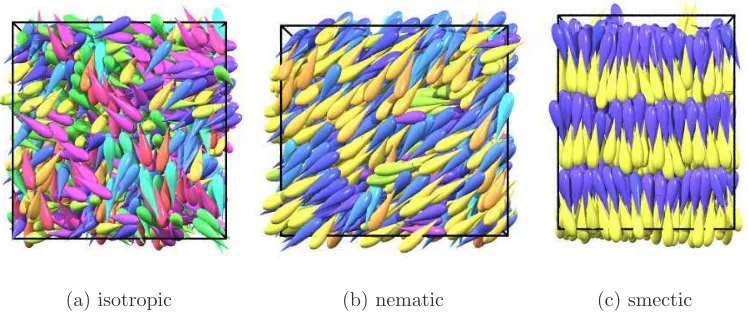
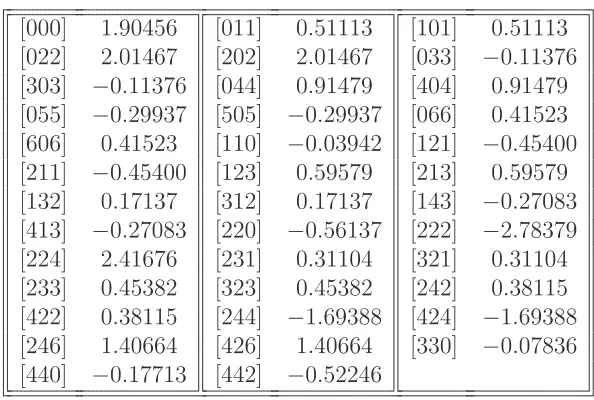
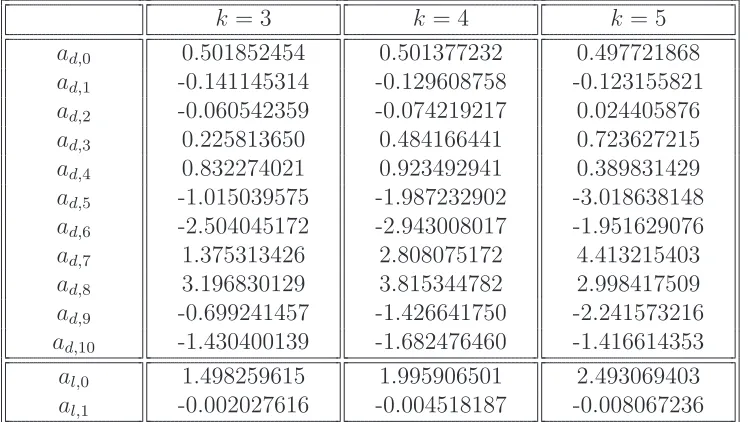
Figure


Related documents
(Note: Bachelor of Music in Music Education students do not enroll in applied lessons during the professional term and are thereby exempt from accompanying
?Peeps? Try to Peck Through a Pension Shell ?Peeps? Try to Peck Through a Pension Shell | 1 ?Peeps? Try to Peck Through a Pension Shell By Kerry Pechter Thu, Apr 5, 2018 A
[r]
It has also been found that women who are active smok- ers and slow acetylators due to their N-acetyltransferase 2 (NAT2) genotype were at increased risk of breast cancer
phenomenological study selected a leadership theory generated in the United States (e.g., Authentic Leadership Theory or ALT) to analyze the perceptions of leaders from three
Keywords: social sustainability, environmental sustainability, social wellbeing, place attachment, social cognitive theory, green space, safety, Urban Mind, London, urban
The mechanism of Detection & prevention of black hole attack on the context of AODV protocol is.. implemented by considering the working of AODV &
( 2011 ) used RNA-seq technology to sequence the leaf transcriptome of Taxus mairei , and obtained 36,493 unigenes, including hundreds of taxane biosynthetic genes and some genes