Big Data Security with Access Control Model and Honeypot in Cloud Computing
Full text
Figure
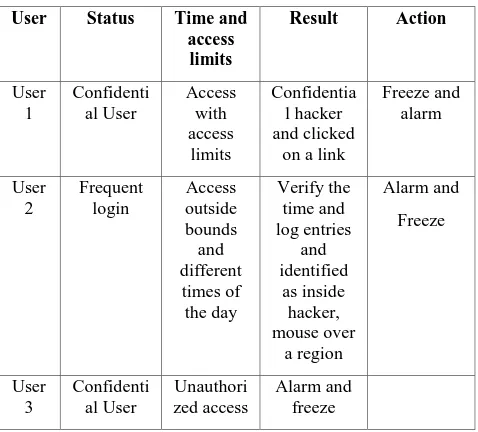
Related documents
tablet computers has the ability to change the dynamic of encounters as it may help share information with patients, foster their education, and eventually enhance patient –
ments in baseline pulmonary function and exercise capacity, as well as significant protection against EIB; the severity as well as incidence of EIB were significantly
In order to evaluate the effects of vehicular emis- sions on pollen viability, different plant species viz ., Cannabis sativa , Hamelia patens , Jatropha panduraefo- lia
Finally, experiments and analyses show that: ① the expected behavior trace of software constructed by training after clustering is more accurate than without clustering; and ②
Background: Repeated injuries, as known as injury recidivism, pose a significant burden on population health and healthcare settings. Therefore, identifying those at risk of
The glass mats with and without binder show different surface topography due to the binder deposition. The binder appears to be present at cross points between fibers as well as along
Dispersion and orientation of multi-wall carbon nanotubes (MWNT) in polypropylene (PP). simultaneously created a tougher and
Forty temperature-sensitive cell division cycle (cdc) mutants of Sac- charomyces cerevisiae were examined for their ability to complete nuclear fusion