Information Security and Computer Fraud
Full text
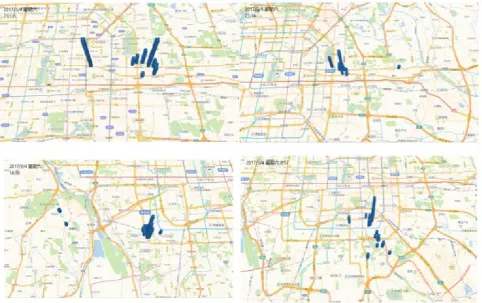
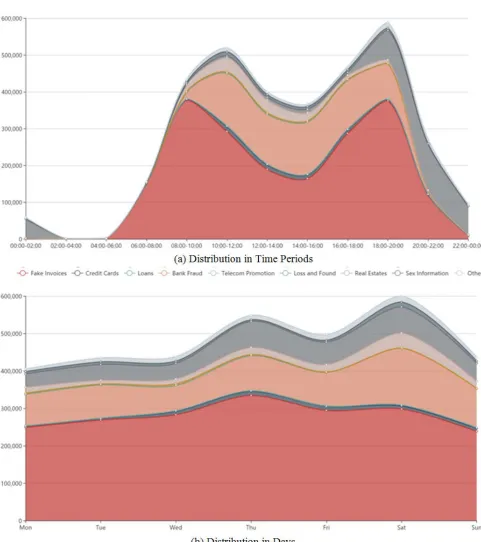
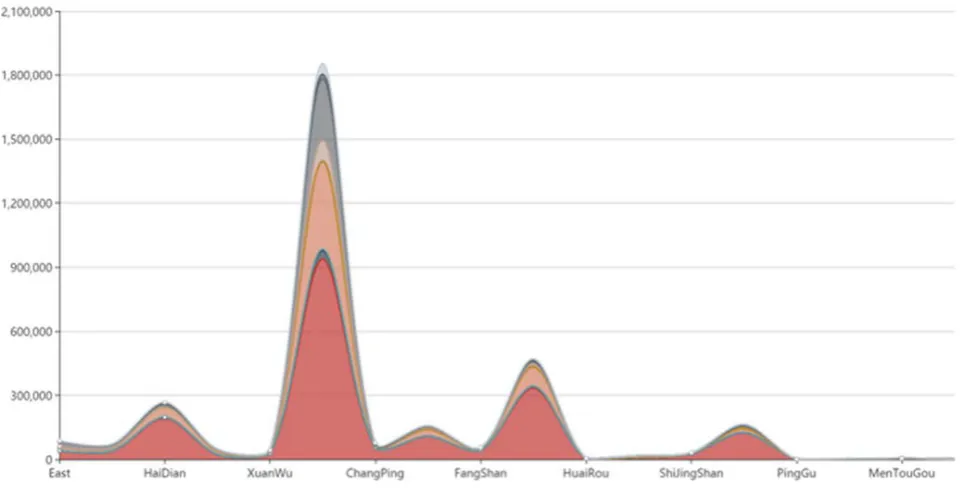
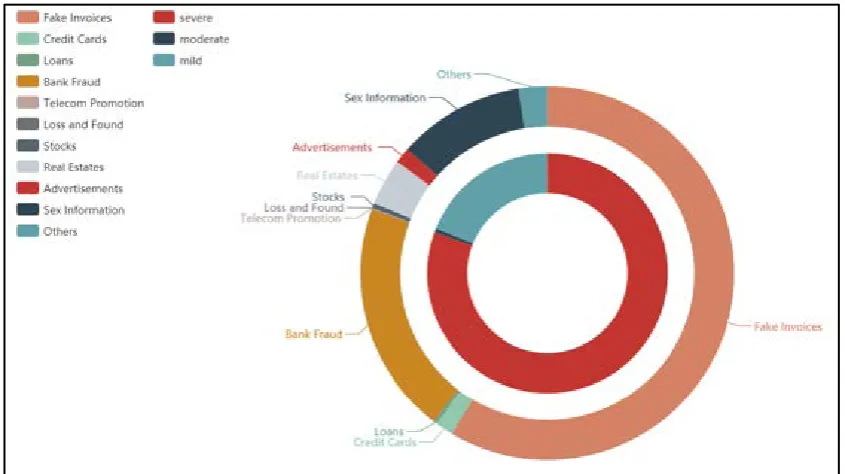
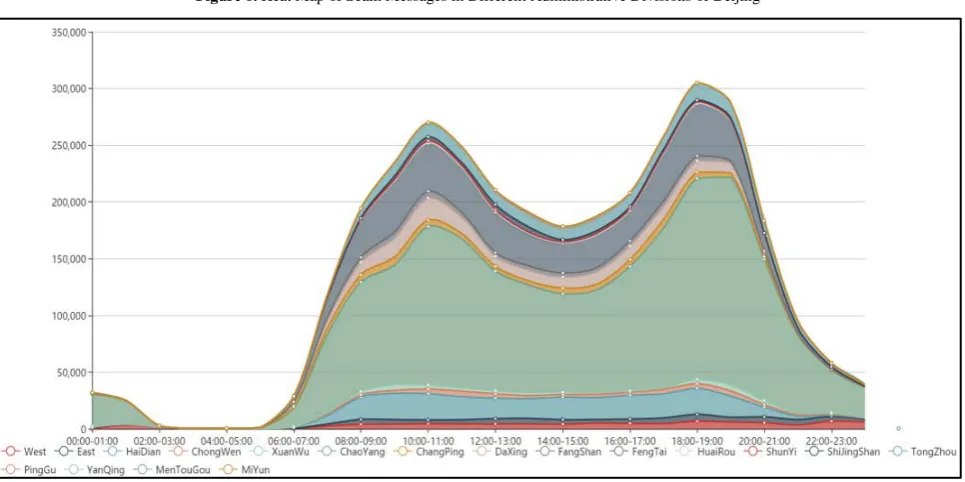
Figure


Related documents
#aptain or First O%%icer can start the #D" Pre%light Proce!ure any time a%ter the Preliminary Pre%light Proce!ure!. All entries must >eri%y -y the
The model on which the Users’ Guide is based is grounded in an organisation development approach which places a strong focus on the people aspects of change.. It is combined
In addition, both the social/personality measures (i.e., academic self-efficacy, academic locus of control, test anxiety and performance-avoidance goals) and
Papain, Trypsin (Plasmin) Calpain I > Calpain II Calpain II > Calpain I Chymotrypsin Thrombin Trypsin, other serine and cysteine proteases (e.g., Bromelain, Ficin, Pa-
As stated above, a solvent company may be dissolved through a voluntary winding up application initiated by company members or its shareholders and/or creditors in
MGT of America performed an annual inspection for compliance with the ICE National Detention Standards (NOS) at the Central Texas Detention Facility (CTDF) located in San
Without opportunities to exercise the skilled moral judgments that the expert application of lethal force requires, what level of ‘moral deskilling’ of professional soldiers
While business travel is currently a small area, it holds the most promising, unexploited growth opportunities of the segments Although commuters have previously driven