Permission-Based Android Malware Detection
Full text
Figure

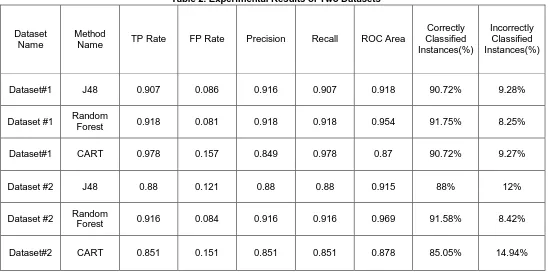
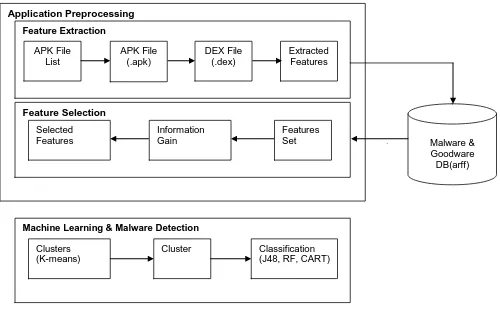
Related documents
Custodial crimes can be reduced in Bihar by 54 percent and 51 percent in Madhya Pradesh, if bad output is weakly disposed, good outputs and inputs are freely
Figure 4.1: Comparison of running time of K-means algorithm on five different inds of platforms (including single core machine) with varying number of clusters k and number of
Downtime Analysis of Tube Filling and Carton Packing Machine at FMCG Company1. Paragjyoti Baishya 1 , Ajoy Krishna
Understanding of determinants of adherence to inhaled medications is important to help create interventions for improving medication adherence in COPD patients. We
Findings of the research indicate that: (i) the image analysis reference method gives reliable data with a minimum of problems and is at a point where the technology can be
index closely matches the swings in inventory change and hence is a leading indicator of business cycles; the PMI-all index matches every business cycle with an
Under most modern secured transactions laws, a valid and enforceable security interest does not achieve its priority status against third parties unless it has been
To the shareholders of Auriga Industries A/S We have audited the Annual Report of Auriga Industries A/S for the financial year January 1 - December 31, 2008, which comprises