A Survey on Potential Applications of Honeypot Technology in Intrusion Detection Systems
Full text
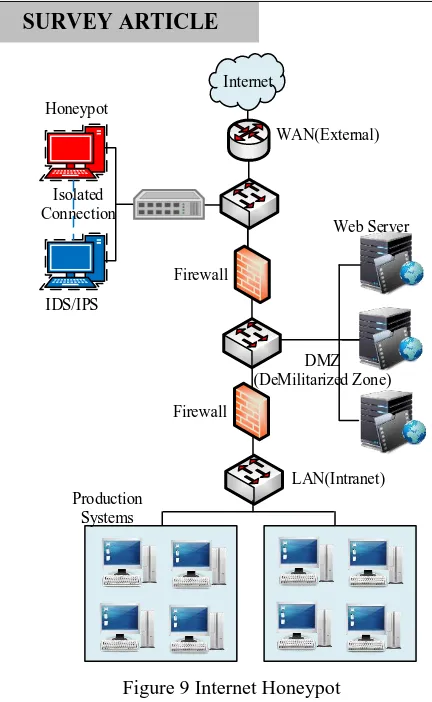
Figure
![Figure 1 Misuse Detection [34]](https://thumb-us.123doks.com/thumbv2/123dok_us/1261998.1631909/3.612.319.555.324.533/figure-misuse-detection.webp)



Related documents
In addition, the nanocrystal thin film showed long-lived confined acoustic phonons corresponding to the ellipsoidal breathing mode, contrary to others work on colloidal systems
A map unit dominated by a soil with a very dark mineral surface horizon, 30 cm thick, with high base saturation, no secondary carbonates, clay illuviation features and
They will continue to be billable under the existing rate codes and may occur on the same date of service (but not the same claim) as an APG visit. 5312 – TB/Directly
Learning from the examples of successful blogs by elementary teachers, four common types of classroom blogs with accompanying examples are shared: Classroom News Blogs, Mirror Blogs,
(Seedlings) Shrub Native 1 100% Live Oak Canopy Status Stem Count % Cover Species.. Restoration Recommendations • 1) Owing to the vitality of the habitat,.. monitoring for
As the leading supplier of trust services for the Internet, VeriSign has successfully issued SSL digital certificates to secure hundreds of thousands of Web sites using a wide range
eVision guides you to select the papers relevant to your programme. If you are enrolling for more than one programme, complete the selection of papers for one
• The sourcing device must see the defined constant load current as the discovery voltage increases from 3 volts to 80% of the maximum output. • At the operating voltage minus 10%