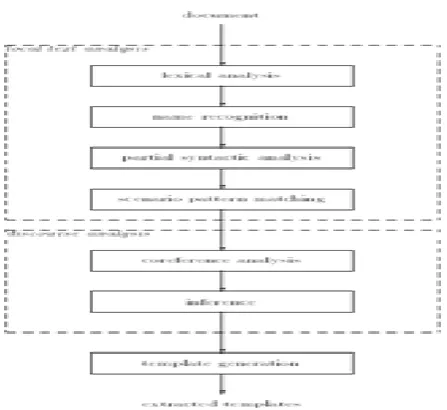
Open Source Intelligence of Web Mining
Full text
Figure
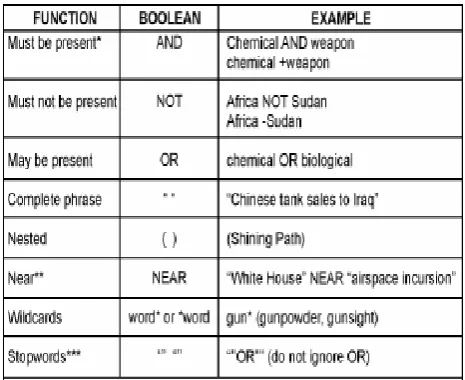

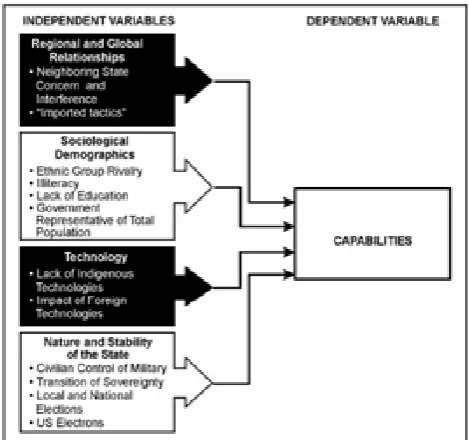
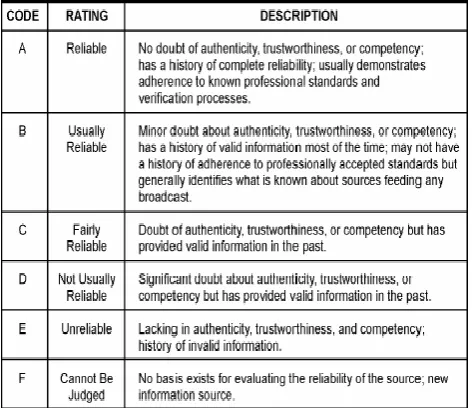
Related documents
Bell-LaPadula: model based on the simple security rule which a subject cannot read data at a higher security level (no-read up) and security rule which a subject cannot
To prevent the packet loss, LTE uses data forwarding from the source eNodeB to the target eNodeB during the handover process.. As soon as the source eNodeB has sent the handover
Now, a lot has been written about the Asiatic Brethren, their members, history as well as their purported influence on later magical and theosophic or- ders.. However, when we dig
Once again, you were presented with a draft of a civil action report and, on 10 December 1998, you submitted a statement which referenced such a report and "concurred that
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
TPI’s Asia Pacific Sourcing Industry Conference (SIC) consistently attracts a significant number of executives representing leading suppliers of sourcing solutions that
o Safe and Supportive Schools Action Plans - $10,000 Superintendent’s Memo: School Choice, 2014-2015 School Year Report: Boston Public Schools Summer Programming 2014 Boston
Strong cities like Warsaw, Cracow, Wroclaw, Poznan, Gdansk and Slaskie area offer a very good level of education, while rural regions and small cities cannot compete