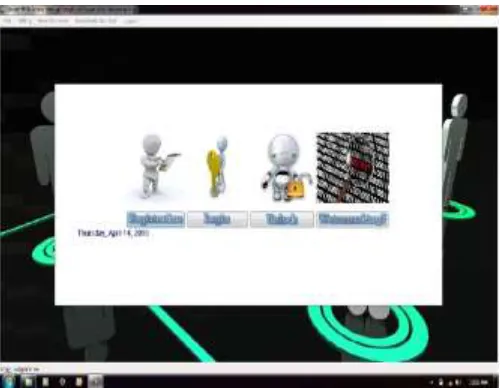
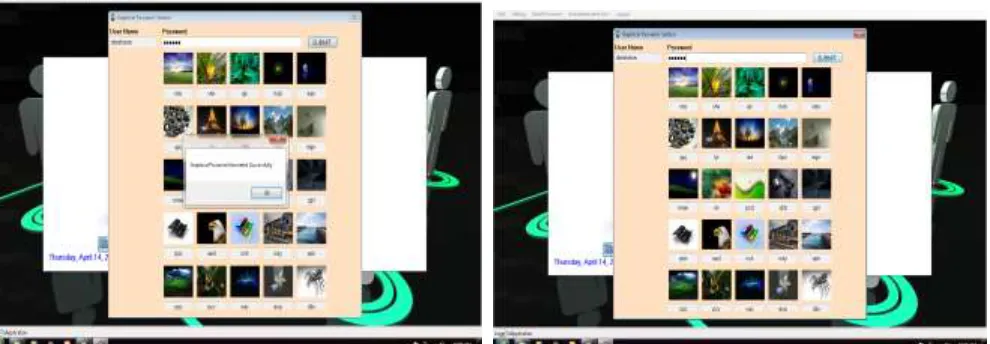
Securing Computer Application Using Image Code as a Password
Full text
Figure
Related documents
In liver cancer, accumulating evidence has demonstrated the existence of a small subset of cancer cells with stem cell properties (self-renewal and differentiation) and several
4.1 The Select Committee is asked to consider the proposed development of the Customer Service Function, the recommended service delivery option and the investment required8. It
1) The versatility and low cost of wet welding makes this method highly desirable. 2) Other benefits include the speed. With which the operation is carried out. 3) It is less
I like The Lord of the Rings because it’s really exciting?. It’s longer than most films, but the actors
Using cross-sectional data from Newsweek’s 2015 Green Rankings List and a variety of online financial sources, this study examines the relationship between corporate sustainability
• The deadline for the part-time evening and part-time Saturday program (including advance standing students interested in these options) will be in mid-May (date to be
organisasjonslæring, arbeidsplasslæring, uformell og formell læring, læring gjennom praksis, sosial praksis og så videre vil derfor være nyttige når man skal foreta en studie
As variable empowerment, education, training, group participation, political affiliation, credit, income and poverty were used.. In the study it was attempted to find a