The impact of security and intelligence policy in the era of cyber crimes
Full text
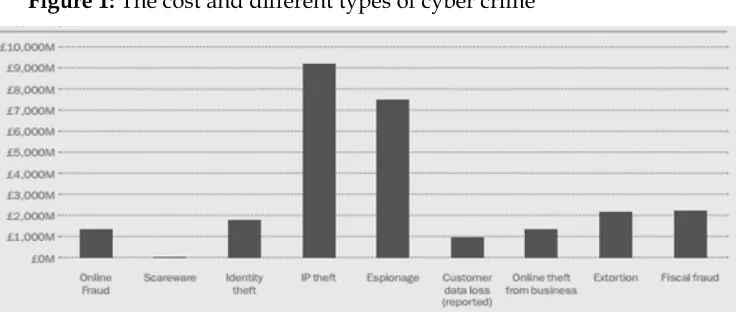
Figure
Related documents
expanding host range of DMV, testified by the present report and by numerous cases of DMV infection reported in the last 5 years in the Mediterranean Sea ( Mazzariol et al., 2013,
ryn March’s study on the Solu Khumbu Sherpa almost 40 years ago (1977), community mountain-closure rituals and practices appear to have been defunct at the time of docu-
потенціалу, до якої поряд з кількісно вимірюваними показниками включено показники якісної оцінки стану регіону, а також методичні
(http://ssubbanna.files.wordpress.com/2012/09/tirupati‑1.jpg)
• There are a broad and growing number of Voice software solutions that provide basic Voice recognition capabilities, Voice application development, WMS or other host connectivity,
Finally, in Section 4 we derive the corresponding best pair of estimators with optimal designs for finite sample size and thus answer the ques- tion of how to plan experiments
mechanistic. Analytical methods are usually including thermomechanical phenomena occurring in cutting process and modeling physical mechanisms during work piece
Most communicators are familiar with the planning process but often don’t know how to integrate digital audiences into the mix.. Your versatile “pocket knife” to hack into