Critical Security Threats in Online Information Systems
Full text
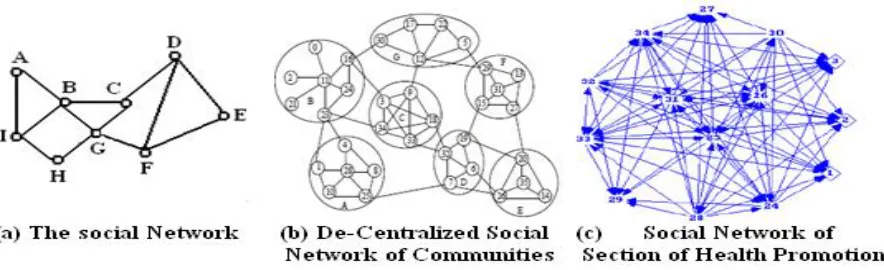
Figure
Related documents
Through the people’s perceptions, this study probed coping strategies as local initiatives being implemented and further adopted as measures to reduce flood vulnerability on
[r]
In light of the Maral decision, the City Council instructed staff to draft an ordinance prohibiting medical marijuana dispensaries within the City, which ordinance has since
The effect of planting with water on early height growth in Zululand North, effect of planting season in both regions and the effect of blanking on final tonnes in Zululand South
In particular, the paper provides an exploration of whether travel distance between tourists' place of residence and the wine region, along with other consumer character-
factor that can contribute 10 effective IS implementation in small businesses. This section examines the attributes of vendor support in greater detail. Table 6 presents
Charles Armstrong (University of Bergen), Paula Henrikson (Uppsala University), Jacob Bøggild (Aarhus University), David Fairer (University of Leeds), Karin Hoff
Along three transects of medium voltage power lines in the steppe of Central Kazakhstan, surveys for bird casualties were carried out in summer 2006 in order to estimate the