Design and Deployment of IPSec VPN Using CISCO Network Infrastructure
Full text
Figure
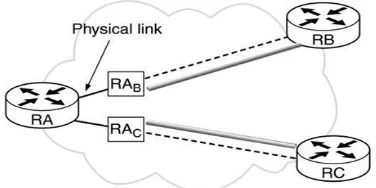
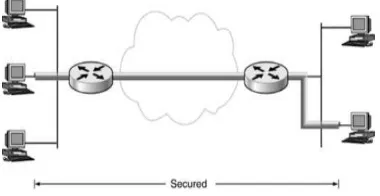
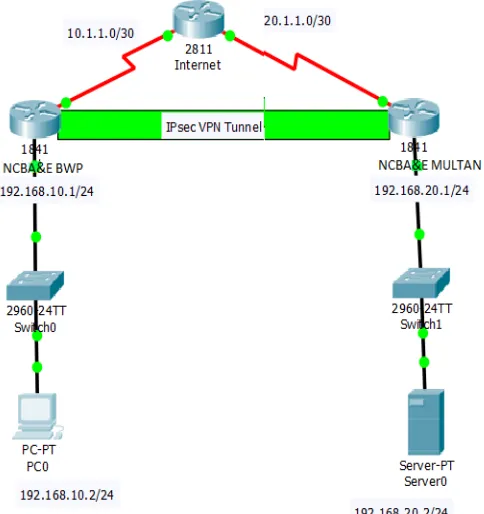
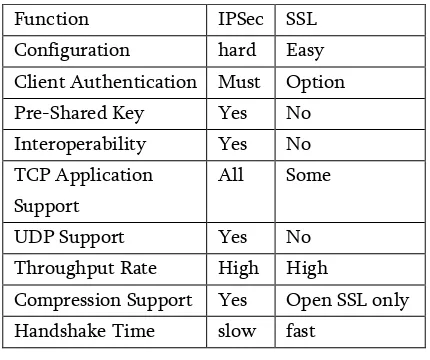
Related documents
Letter from Washington D.C. office of Peat, Marwick, Mitchell & Co.. business operations that paid interest or dividends to nonresident aliens or foreign
limits of first amendment protection for attorneys' advertisements by distin- guishing between in-person solicitation and solicitation by letter. 25 This dis- tinction
To determine whether the Envs, isolated from HIV-1 viral particles of different individuals, are responsible for the poor ability of these viruses to replicate, we first expressed
The inherent power models, especially those at the end of the continuum, are the most boundless. The courts that follow them have the widest range of sources and the
The absolute amount of MeHg produced increased with the cysteine concentration in the medium, as did MeHg production normalized to cell protein, with the most MeHg production in the
The Senate proponents also asserted that this nonuniform amendment would prevent creditors with stale claims from harassing a debtor's transfer- ees. The UFTA,
The Llano decision has a major fault. The court claimed to be construing the second force majeure provision according to commercial standards that were recognized as
To gain insight into the effects of pneumococcal EVs on host cells, we incubated A549 lung epithelial cells with EVs from strain T4 or its isogenic mutant deficient in pneumolysin