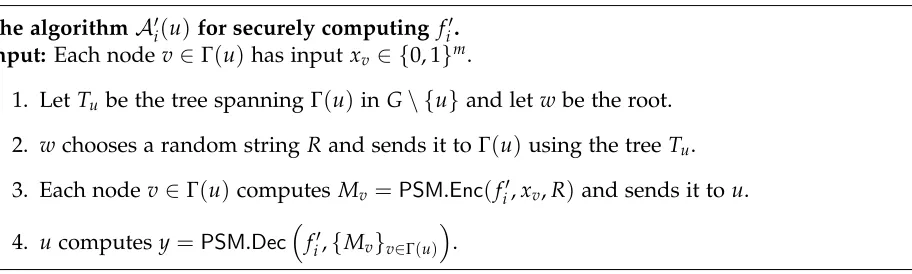
Distributed Algorithms Made Secure: A Graph Theoretic Approach
Full text
Figure




Related documents
Faculty demographics (age, gender, degree held, ACHE board certified, number of years of health care management experience, number of years as faculty member, training in
The Registrar General is the Head of the General Register Office and makes regulations and issues instructions to be followed by registration officers in carrying out their
Alexander Klein; CIAM; collective dwelling; domestic space; housing crisis; Karel Teige; minimum dwelling; rationalization; Taylorism; universal
World Investment Report (WIR 2009). Transnational Corporations, Agricultural Production and Development , rapport publié par United Nations
Saturday, June 7, 2014 Thinking Outside the Box?: Take Your Research to a New Level This conference is sponsored by the York County Heritage Trust and South Central
Success was not yet assured. In about a year, reserves would be transferred over from correspondents to the Reserve Banks under the new reserve require- ments. As we noted
However, cybersecurity has become a critical challenge in the IoT enabled cyber phys- ical systems, from connected supply chain, Big Data produced by huge amount of IoT devices,
American courage and American idealism, together with the sound common sense of the American people, summon us to the defense both of our physical security and of those moral