Strong Authentication for Cloud using Image Based OTP & User Profile
Full text
Figure



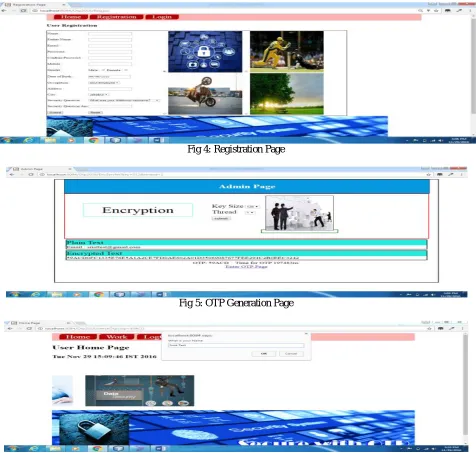
Related documents
CipherCloud is the industry leader in cloud information protection, enabling organizations to securely adopt cloud applications by overcoming data privacy, residency, security,
There are several specific sequences in chapter 9 which use the General Call Address (0x00) to send commands instead of data to the FT201X. These are demonstrated in the example
Katherine Anne Porter’s Early Stories: Successful Narrators and Katherine Anne Porter’s Early Stories: Successful Narrators and Unsuccessful Characters.. Unsuccessful Characters
11-12.RL.1 Cite strong and thorough textual evidence to support analysis of what the text says explicitly as well as inferences drawn from the text, including determining where
PCA analysis supports the concept that caries risk is divisible into patterns attributable to distinct risk factors that work in accord: in the total sample two different
The set of genes (blue lines consisting of yellow pixels in Figure 2-a) is generated inside the building footprint (Red rectangle in Figure 2-a) using the DDA (Digital
Dr Miller says about this verse: “ One of the well known scientific prin- ciples is the principle of finding mistakes or looking for mistakes in a theory until it’s proved to be
While both cases show that networking also built capacity for the projects, as niche literature suggests (e.g. Geels and Deuten, 2006; Hargreaves et al., 2013; Raven et al.,