Anomaly Detection Using Context-Based Intrusion Detection System
Full text
Figure
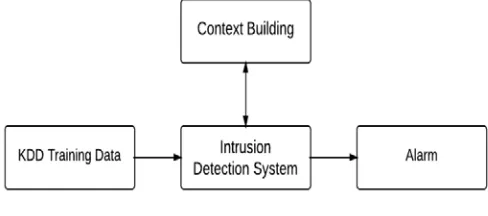
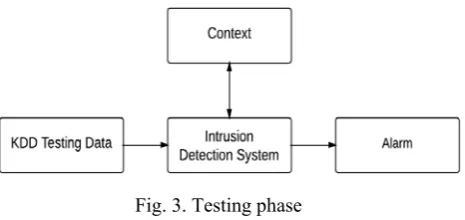
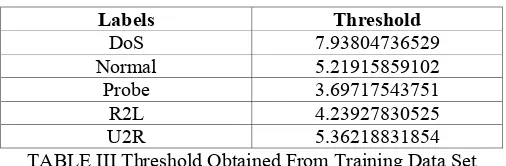
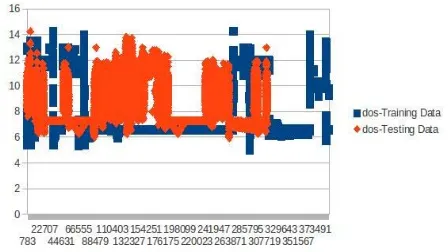
Related documents
Research tasks: - to find appropriate conservation methods of seed of the wild plants of Kazakhstan; - to test the available techniques in the conditions of the seed bank of
Learning from the examples of successful blogs by elementary teachers, four common types of classroom blogs with accompanying examples are shared: Classroom News Blogs, Mirror Blogs,
Dickinson (1995) found that individuals with positive perceptions of classroom or school environment enhance their learning and motivation by adapting mastery
Figure 5.34 Temperature and species mole fraction distributions on two perpendicular vertical center-planes inside gasifier for concentric coal-oxidant injection case using
In the following steps, you’ll install the legs at the front of the cabinets, and secure a cabinet support board to the wall.. This is a length of particleboard packed together
He has been a Senior Fellow for Eurasia and Fellow for Transatlantic Energy Security at the Atlantic Council, a Visiting Fellow with the Russia and Eurasia Program at the Center
12.1 The Organizing Committee shall establish simplified customs procedures through the customs consultative committee, and details of the applicable custom