DH EAACK Secure Intrusion Detection System to detect Black Hole Attack in MANET
Full text
Figure
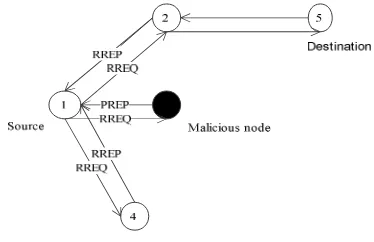


Related documents
(MT1131), ⌬ ccoA (SE8), and ⌬ cutO (SE15) strains under anaerobic photosyn- thetic growth conditions on MPYE medium were determined as described in Materials and Methods.. Filter
The inclusion criteria for Group 2 were 1) patients who underwent lung function test without a bronchodilation test and 2) CT images reconstructed using a standard (or B26, B30,
Vol 10, Issue 4, 2017 Online 2455 3891 Print 0974 2441 FABRICATION OF NOVEL ANTICANCER POLYOXOMETALATE [COW11O39(CPTI)] 7 CHITOSAN NANOCOMPOSITE, ITS TOXICITY REDUCTION, AND SUSTAINED
Solnica Krezel 1 pm The homeoprotein Bozozok and the Zebrafish organizer 299 The role of the homeodomain protein Bozozok in Zebrafish axis formation LILIANNA SOLNICA KREZEL1 and
16-kb Hin dIII fragment containing the distal Os micro-injected FVB/N mouse embryos with a linearized mouse BAC clone (96h13) that spans the distal break breakpoint contains a
Based on this technique we investigate the minimal effort for an adversary to obtain a failure in 3 cases: when he has access to a quantum computer, when he mounts a multi-target
(The smaller deletions are operationally equivalent to the l(2)gl mutants occurring in wild populations of D. melanogaster.) These facts are con- sistent with the