On the Penetration of Business Networks by P2P File Sharing
Full text
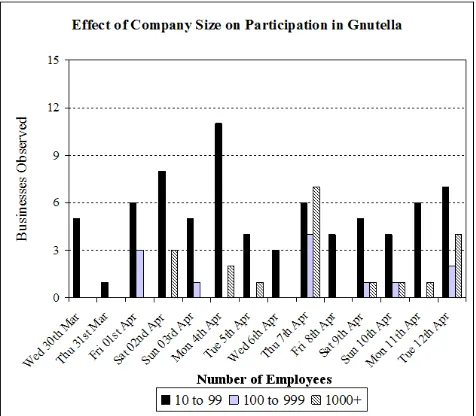
Figure

Related documents
This project seeks to strengthen the infrastructure behind using Wikidata (Vrande č i ć 2012) to mobilize Linked Open Data for knowledge discovery in scholarly and other contexts,
Abstract : Distribution or self storage business alone gradually highlights the high cost, low efficiency drawbacks, how to carry out joint enterprises specialized joint
Township officials, police department representatives, members of our Community Board on Police and a representative from the New Jersey Attorney General’s office will join the
In order to determine if prior settings in early learning had an impact on Kindergarten Readiness as measured by the Brigance Kindergarten Screener, scores of students who had
metric estimation and identiÞcation of scalar additive hedonic models (Eke- land, Heckman, and Nesheim, 2002) and scalar nonadditive hedonic models (Heckman, Matzkin, and Nesheim,
3.4 Respondents broadly embraced the concept of choice, suggesting that it should be core to the business of mental health nursing. Many suggested, however, that a realistic
Achieving a rich, safe, and secure “Advanced Information Society” − Overview: Interim Report of “Study Forum for Dependability & Security of Information Systems & Software
As seen in Figure 10 , PolyCubes computed by our method nat- urally capture the major features of complex models, includ- ing off-axis and sharp features of CAD models and