Cyber risk management for wireless communication in organization
Full text
Figure
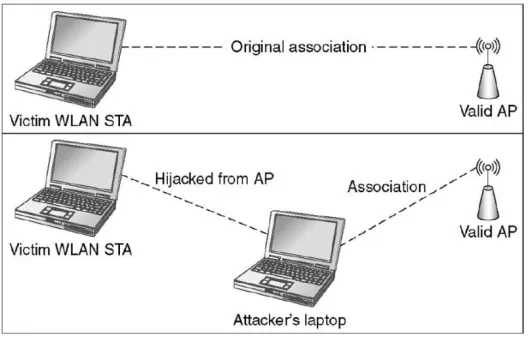
Related documents
On a review, the Superintendent must confirm the prohibition ifhe is satisfied that that driver operated, or had care and control of~ the motor vehicle and had consumed alcohol
Keywords: extracellular matrix, cancer therapy, drug transport, immunotherapy, chemotherapy (CH), radiotherapy, tumor microenvironment,
Support of BP MS 150 Recommended Training Rides – BP MS 150 Ride Marshals, wearing Ride Marshal apparel, must support in at least two BP MS 150 Spring Recommended Rides. Supporting
Shohibulfalahah berkata : jika abu daun yaqtn (labuh) diletakkan dibawah pohon jeruk maka banyak buahnya dan tidak ada yang jatuh sama sekali, daunya jika dikunyah maka memotong
drilling fluids with different viscosity properties in order to compare settling velocity of the particles. These fluid samples are categorized into three groups:.. 20%
This course is a survey of the major approaches to counseling and psychotherapy, including psychodynamic, existential/humanistic, behavioral, cognitive-behavioral, group, and
2004 / ///// The!Art!Faculty!Exhibition!2004,/The/University/of/Connecticut/William/Benton/Museum/of/Art,/Storr/CT,/Aug/31/–/ Oct10,/2004.//
If exposure limits may possibly exceed the TLV or respiratory irritation is experienced, NIOSH/MSHA approved respiratory protection should be worn. An industrial hygienist or