Equilibrium, thermodynamics and kinetics study of doxycycline adsorption from aqueous solution using spent black tea leaves and pomegranate peel wastes
Full text
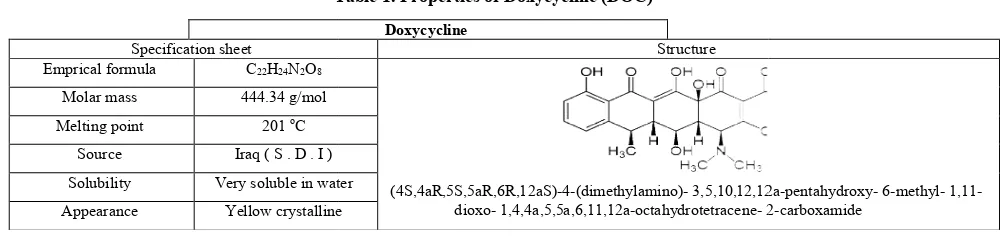
Figure



Related documents
In this section, we study two uniqueness theorems for the solution of the inverse problem associated with L , first by the Weyl-Titchmarsh m- function, and second by nodes of L. Then,
“ Tick, Tack, Toe the Line: Lyme Disease and What to Do ” Think IPM Blog , New York State Integrated Pest Management Program, Cornell University, 18 July 2018. •
Document Image Retrieval System (DIRS) based on keyword spotting performs matching process directly on data images using word-images as queries. It usually compares
To calculate the contribution of the reforms to recent growth performance in Latin America, we calculated fitted values using both versions of equation (1) for each of the
Qualitative analysis shows the cross-linguistic influence of L1 (Arabic) in learning the grammatical items of English in general. This study is the outcome of the
We analyzed the genetic diversity, temporal distribution, demographic history and the spatial diffusion pattern of norovirus that circulated in China by using a Bayesian coales-
In this exercise, we have presented a case for a new method of computing the VaR for a set of fixed income securities based on extreme value theory that models the tail
At the same time, forward security forces us to compute authentication tags per sensed unit of data, which we refer to as a message from now on.. 3 Therefore,