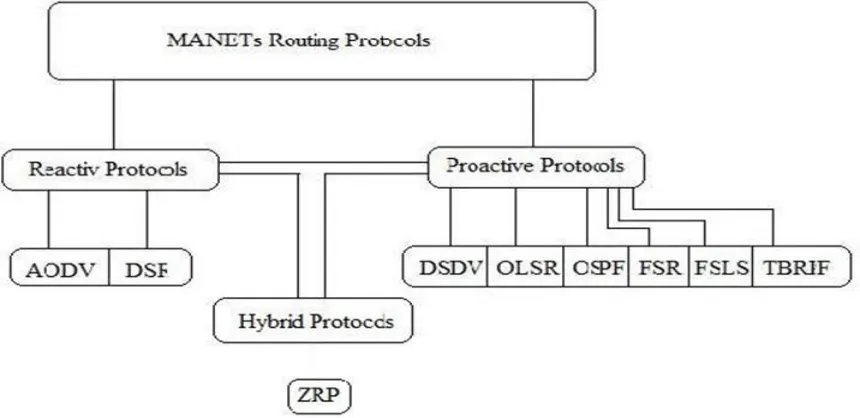
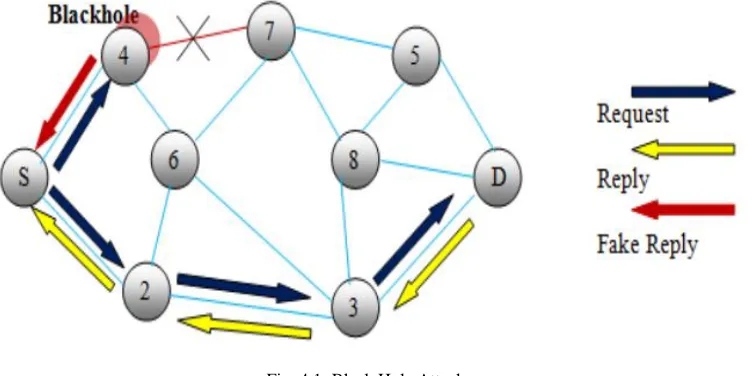
A Survey on How Black Hole and Worm Hole Attack evolves on AODV Routing Protocol
Full text
Figure


Related documents
The charges brought by the Commission (and upheld by the CFI following an appeal) alleged that Microsoft was limiting market access for other business enterprises by refusing to
The Daylight Spectrum Index (DSI) is defined as the ratio of the area defined by the photopic perception of the Spectral Power Distribution of the studied light source and
Participants who followed the career path pursued postsecondary education for economic gain and completed a number of courses, a certificate or an associate’s degree at a
Apart from direct service delivery, ANMs were required to do several programmatic (records and reports), programmatic support (meetings, trainings, etc) and non-health
SEFI Single-Event Functional Interrupt SEGR Single-Event Gate Rupture SEL Single-Event Latchup SET Single-Event Transient SEU Single-Event Upset. SOHO Solar &
the slum was not located on land designated for city infrastructure improvements (e.g. new roads or riverfront development) and the slum was not located in a hazardous area..
The pedagogical implications of the aforementioned issues, according to Gee (2015, p. 115), may be for “the teaching of language and literacy to people new to a culture and
This survey is being done to find out the opinions and actions of residents like yourself who live in flood prone areas about homeowner mitigation (making changes to your home