Public auditing with cloud based group user revocation with data integrity
Full text
Figure
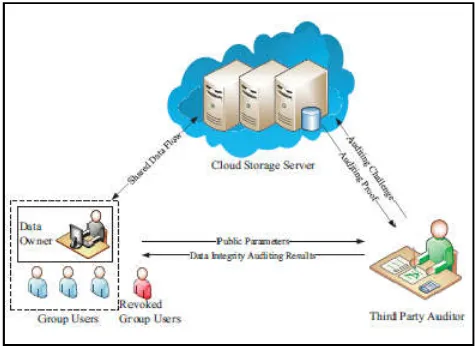
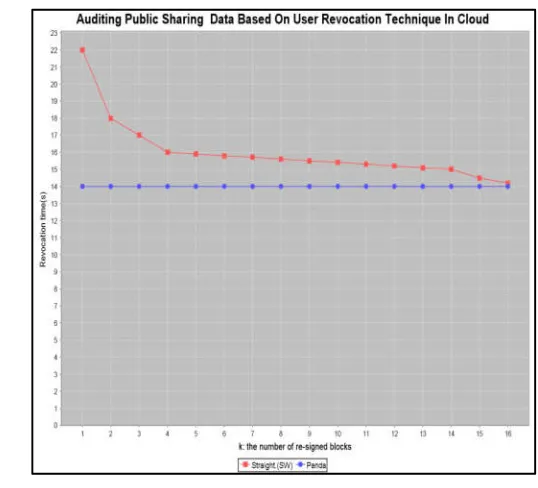
Related documents
Low energy particle experiments?electron analyzer (LEPe) onboard the Arase spacecraft Kazama et al Earth, Planets and Space (2017) 69 165 https //doi org/10 1186/s40623 017 0748 6 F U L
Vol 7, Issue 5, 2014 ISSN 0974 2441 CHEMICAL CHARACTERIZATION AND BIOLOGICAL ACTIVITIES OF EXTRACTS OFTHREE PLANTS USED IN TRADITIONAL MEDICINE IN BENIN TECTONA GRANDIS, UVARIA CHAMEAE
Neelesh Raghuwanshi et al.[2] presume that with the expansion of RBI Grade-81 the plastic furthest reaches of soil increments and fluid point of confinement of soil abatements
Genomic DNA from six individuals was prepared for whole- genome sequencing: diploid Col-0 #1 (used to normalize data from the other individuals), diploid Col-0 #2 (control),
Similar to the above results effluent treated with Nymphaea nouchaliexhibited lowest concentration of nitrogen with 39 mg/ml followed by Musa paradisiaca and
• In the classic ASME NB-3600 procedure only scalar stress differences are used and the actual time and location of the stress in the pipe cross section is lost.. To study the
As such, what ends up happening is that one of the later age ranges (suppose the 50 target for this example) already has a model output above the desired target. 3) The
In Chapter 4, we focus on statistical topic modeling for networks and develop a Relational User Interests (RUI) model as a generalization to the Relational Topic Model (RTM) in