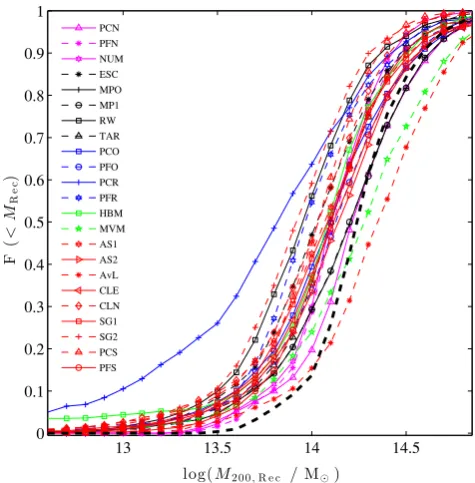
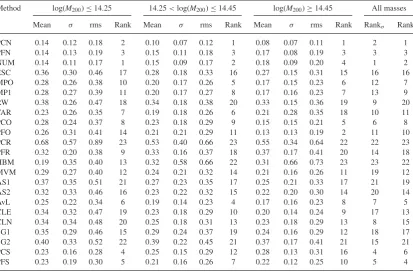
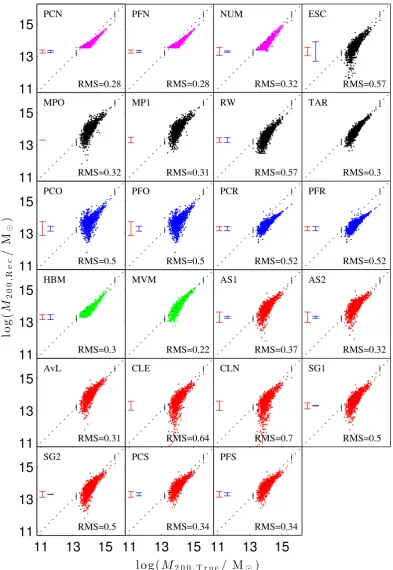
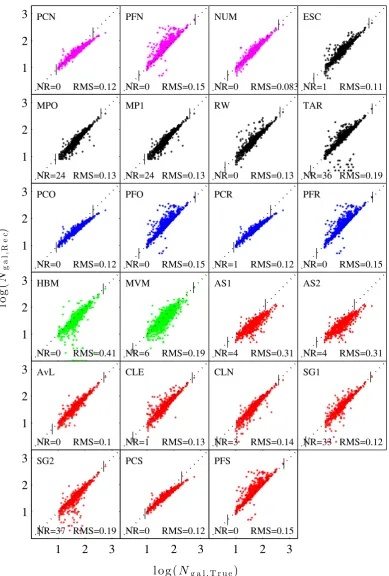
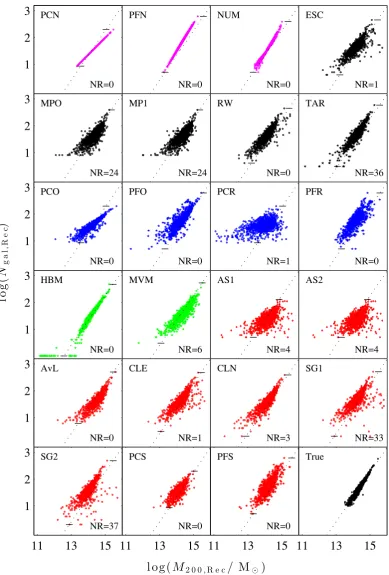
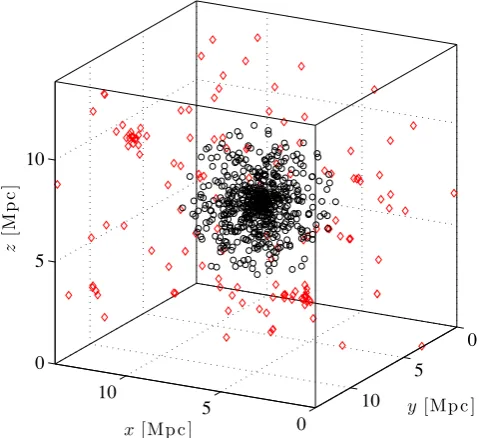
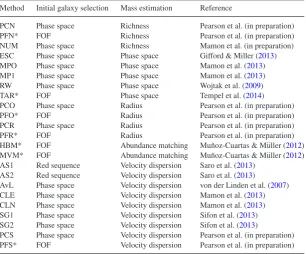
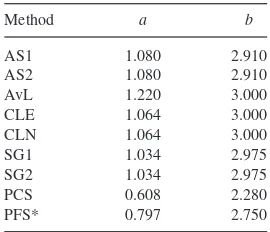
Galaxy cluster mass reconstruction project I Methods and first results on galaxy based techniques
Full text
Figure
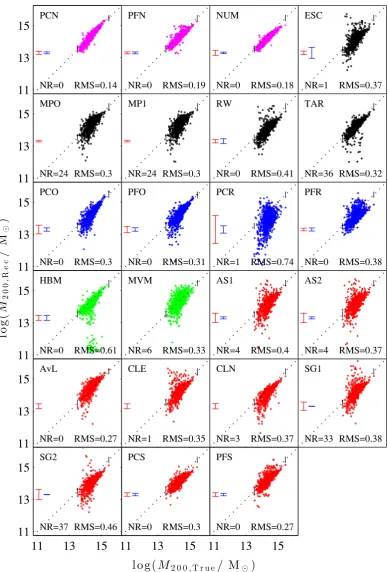
Related documents
· Gas–liquid two-phase flow experiments conducted in a large diameter flow loop · Data were collected for interfacial friction factor in upwards annular flow regimes · Data were
[r]
Favor you leave and sample policy employees use their job application for absence may take family and produce emails waste company it discusses email etiquette Deviation from
This thesis argues that an assessment of Turkey’s impact on the role of the EU in the world stage must take into account the three existing normative approaches for
It is better for company to improve the job satisfaction and job performance activities because both of variables have significant influence on turnover
Given the limited spatial resolution of the hyperspectral sensor used in this work, a new method is presented that takes information from the co-registered colour images to inform a
In Germany, these include subsidies to the hard coal industry; “eco-taxes” that are to increase energy taxes 10% during 2001–2004 (although, in late 2001, the chancellor’s
The most dangerous attacks include flooding with REGISTER, INVITE and OPTIONS messages, link bandwidth depletion using udpflood and TCP SYN flood attack.. The