Hardware/Compiler Memory Protection in Sensor Nodes
Full text
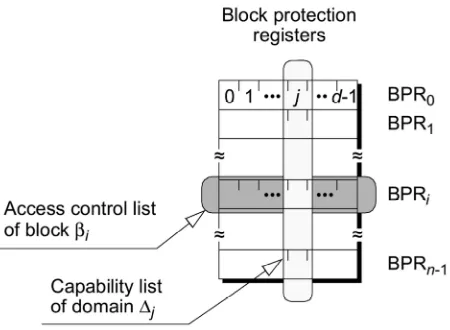
Figure

Related documents
Wklv sdshu lqyhvwljdwhv wkh uroh ri d up*v rzqhuvkls frqfhqwudwlrq lq doorzlqj vkduh0 kroghuv wr frpplw qrw wr h{huflvh wkhlu frqwuro uljkwv wr wkh ghwulphqw ri ghewkroghuv1
Set by default to 20% of the value (revenue) per customer per year. The total number of unique visitors to the web site per day. Set by default to be 0.1% of the number of customers
If , number of different nodes desired to keep a copy of data, is initialized to zero, the mobile sensor nodes in the network will not forward or receive a data packet and will
The summary resource report prepared by North Atlantic is based on a 43-101 Compliant Resource Report prepared by M. Holter, Consulting Professional Engineer,
Facts: PO2 Masi dispatched PO1 Pacis and PO1 Labaclado of the Station Anti-Illegal Drugs Task Force to conduct surveillance in Sampaloc St., Camarin, Caloocan City because of
Voor veel van de maatregelen is die grondslag te vinden in artikel 7 Wpg, een bepaling die de regering de bevoegdheid geeft leiding te geven aan de bestrijding van een
After having considered the evidence presented, the testimony of the witnesses and taking official notice of its file in its matter, the Board voted to place the Respondent’s
Selected generic drugs Retail: $0 copay/prescription Mail order: $0 copay/prescription Not covered Covers up to a 30-day supply (retail prescription); 90 day supply (mail