Abstract: Aimed at finding appropriate QMS (quality management system) in HE (higher education) organisation, this paper introduces quality management framework at higher education study using RFID. To achieve good quality of all the faculty, this paper promoting the intelligent use of information technology. This paper will systematically address many of the challenges transported more sharply into focus by information technologies. RFID is used more effectively for faculty attendance system. This paper is used for motivating faculties to work in the best interests of the organization; and monitoring and evaluating progress of each each faculty toward goal achievement. Faculties in and out entries is being verifies against RFID entries. So by this way this study provides dual authentication for faculty attendance and management system.
Keyword: Faculty Attendance System, RFID (Radio Frequency Identification), HE (Higher Education), QMS (Quality Management System), EPC (Electronic Product Code), LF (Low Frequency), RD (Radio Frequency).
1. INTRODUCTION
“Time is that quality of nature which keeps events from happening all at once. Lately it doesn’t seem to be working”
The recent decade has brought extraordinary public demands for higher quality in colleges and universities. Higher education institutions today are under increasing pressure to introduce some system for monitoring or assessing faculty quality and faculty regularity in the organisation.
The role and importance of higher education in culture have changed dramatically over the years. Radio frequency identification (RFID) technology has evolved since, and has been implemented in various applications, such as in Warehouse Management, Library System, Theft Prevention, Toll Collection System and so on. To solve all problems & to manage the faculty attendance in a most efficient way, use RFID technology along with biometric technology. RFID attendance system provides robust, secured and automatic attendance management in Educational campuses with minimum human involvement. Its ability to uniquely identify each faculty based on their RFID tag / thumb impression makes the process of taking the attendance automatic, faster and secured as compared to conventional method. The ID cards of the faculty is embedded with RFID tag which is read by a reader. This RFID system is interfaced to a database through a computer or some electronic circuits.
This method is more effective to prevent problem encountered till now.
RFID is a emerging technology, deeply rooted by its early developments in using radar 1 as a harbinger of adversary planes during World War II. A plethora of industries have leveraged the benefits of RFID technology for enhancements in sectors like military, sports, security, airline, animal farms, healthcare and other areas. Industry specific key applications of this technology include vehicle tracking, automated inventory management, animal monitoring, secure store checkouts, supply chain management, automatic payment, sport timing technologies, etc. This paper introduces the distinctive components of RFID technology and it focuses on its core competencies: scalability and security. It will be then supplemented by a detailed synopsis of an investigation conducted to test the feasibility and practicality of RFID technology. Radio-frequency identification (RFID) is a technology that uses radio waves to transfer data from an electronic tag – called an RFID tag or label, which is attached to an object – through a reader for the purpose of identifying and tracking the object.
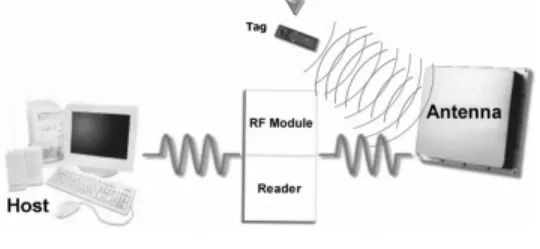
A complete RFID system consists of a transponder (tag), reader/writer, antenna, and computer host. The transponder, better known as the tag, is a microchip combined with an antenna system in a compact package. The microchip contains memory and logic circuits to receive and send data back to the reader. These tags are classified as either active or passive tags.
Tags could also be classified based on the content and format of information. The classifications range from Class 0 to Class 5. These classes have been determined by the Electronic Product Code (EPC) Global Standard. In the table below, classes refer to a tag’s basic functionality (i.e., it either has a memory or an on-board power), while generation refers to the tag specification’s major release or version number. The class structure for the tags is shown in the table below.
Table 1 Class Structure for Tags
EPC Class
Definition Programming
Class-0 Gen-1
Read only, Passive tags Programmed by the factory Class -
1Gen-1
Write once, read- many, passive tags
Programmed by the user and then locked
Class- Write-many, read- Programmed by
RF Attendance System Framework for
Faculties of Higher Education
Ms. Unnati A. Patel1 Dr. Swaminarayan Priya R2
1
Asst. Professor, M.Sc(IT) Department, ISTAR, V.V.Nagar-388120, India
2
1Gen-2 many, passive tags the user and then locked Class-2 Rewritable passive tags
with extra functionality, including encryption and emulation Can be reprogrammed
Class-3 Semi-passive tags that support broadband Communication Class-4 Active tags that can
communicate with other peers Class-5 Readers, they can
power other tags of Class 1, 2 and 3, can communicate with Class 4
wirelessly
Not applicable
2. EVOLUTION OF RFID:
The success of RFID technology primarily centres on the advent of radio technology. The developments in radio technology were a prerequisite to harness the essence of RFID technology. There is significant growth over the past couple of decades in this technology (see Figure 1). RFID technology is rife in modern industries that demand data integrity and high efficiency of the system. This technology is used for tracking vehicles and goods, courier services and luggage handling. Other applications include animal tracking, secure toll payments, inventory management systems, access control mechanisms, etc. Figure 1 depicts the evolution of RFID technology.
Figure 1 Evolution of RFID
3. PROBLEM
Before few decades, faculty presence in higher education is being taken by keeping register and in that all faculties were doing Absent (A) or Present (P). But in that system,
there is one problem: if faculty remains absent on any day and on next day he/she marks presence (P) of previous day then management sometimes unaware about this. Another problem is that, any employee can mark present of any other employee because at that time no authentication is there. After few years, the system of marking signature in register came. So that other faculty cannot mark present in place of any other. But situation is not stable in those years also, because a faculty came to organisation and can mark present and then he leave the organisation for doing his personal work. Then management is totally unaware about this thing. This is the main problem even in todays HE system also. If the organisation is big, then there were no. of faculties and it is not feasible to check each and every faculty’s status manually. After few years, for faculty attendance, biometric system (thumb impression checking) came. Now a days, this system is being used by most of the HE persons. But even this system is not so successful and trustable because any faculty can mark present and then go outside for his/her personal work without punching.
4. WHAT IS RFID?
RFID is short for Radio Frequency Identification. Generally a RFID system consists of 2 parts: A Reader, and one or more Transponders, also known as Tags. RFID systems evolved from barcode labels as a means to automatically identify and track products and people.
4.1 COMPONENTS OF RFID:
A typical RFID system is made up of three components: Tags (RFID ID Cards), Readers and the host computer.
Tag (RFID ID Cards):An RFID tag is comprised of a microchip containing identifying information and an antenna that transmits this data wirelessly to a reader. At its most basic, the chip will contain a serialized identifier, or license plate number, that uniquely identifies that item, similar to the way many bar codes are used today. A key difference, however is that RFID tags have a higher data capacity than their bar code counterparts. This increases the options for the type of information that can be encoded on the tag, including the manufacturer, batch or lot number, weight, ownership, destination and history (such as the temperature range to which an item has been exposed). In fact, an unlimited list of other types of information can be stored on RFID tags, depending on application needs. An RFID tag can be placed on individual items, cases or pallets for identification purposes, as well as on fixed assets such as trailers, containers, totes, etc. Tags come in a variety of types, with a variety of capabilities. Key variables include: "Read-only" versus "read-write". There are three options in terms of how data can be encoded on tags: (1) Read-only tags contain data such as a serialized tracking number, which is pre-written onto them by the tag manufacturer or distributor. These are generally the least expensive tags because they cannot have any additional
information included as they move throughout the supply chain. Any updates to that information would have to be maintained in the application software that tracks SKU movement and activity. (2) "Write once" tags enable a user to write data to the tag one time in production or distribution processes. Again, this may include a serial number, but perhaps other data such as a lot or batch number. (3) Full "read-write" tags allow new data to be written to the tag as needed—and even written over the original data. Examples for the latter capability might include the time and date of ownership transfer or updating the repair history of a fixed asset. While these are the most costly of the three tag types and are not practical for tracking inexpensive items, future standards for electronic product codes (EPC) appear to be headed in this direction.
RFID tags are further broken down into two categories: - Active RFID Tags are battery powered. They broadcast a signal to the reader and can transmit over the greatest distances (100+ meters). Typically they can cost Rs. 500 or more and are used to track high value goods like vehicles and large containers of goods. Shipboard containers are a good example of an active RFID tag application.
- Passive RFID Tags do not contain a battery. Instead, they draw their power from the radio wave transmitted by the reader. The reader transmits a low power radio signal through its antenna to the tag, which in turn receives it through its own antenna to power the integrated circuit (chip).
Figure 2 RFID Tags
Reader: An RFID reader is a device that is used to read RFID tag data. The reader has an antenna that emits radio waves; the tag responds by sending back data stored in it to Reader.
Figure 3 RFID Reader
Host Computer: It reads/writes data from / to the tags through the reader. It stores evaluates obtained data and links the transceiver to applications
5. HOW RFID WORKS?
Shown below is a typical RFID system. In every RFID system the transponder Tags contain information. This information can be as little as a single binary bit, or be a large array of bits representing such things as an identity code, personal medical information, or literally any type of information that can be stored in digital binary format.
Figure 4 RFID Working Flow
Shown is a RFID transceiver that communicates with a Tag. There are two types of tags: Active Tags and Passive Tags. When the Tag enters the generated RF field it is able to draw enough power from the field to access its internal memory and transmit its stored information. When the transponder Tag draws power in this way the resultant interaction of the RF fields causes the voltage at the transceiver antenna to drop in value. This effect is utilized by the Tag to communicate its information to the reader. The Tag is able to control the amount of power drawn from the field and by doing so it can modulate the voltage sensed at the transceiver according to the bit pattern it wishes to transmit.
6. DIFFERENT TYPES OF RFID
There are several versions of RFID that operate at different radio frequencies. The choice of frequency is dependent on the business requirements and read environment. Three primary frequency bands are being used for RFID:
- Low Frequency (125/134KHz) – Most commonly used for Attendance & access control.
- High -Frequency (13.56 MHz) – Used where medium data rate and read ranges up to about 1.5 meters are acceptable. This frequency also has the advantage of not being susceptible to interference from the presence of water or metals.
- Ultra High-Frequency (850 MHz to 950 MHz) – offer the longest read ranges of up to approximately 3 meters and high reading speeds.
7. KEY BENEFITS OF RFID
RFID-enabled systems help companies cut costs, improve customer service, reduce labor, increase accuracy, and improve production throughput. Other benefits of RFID technology are as listed below:
No line-of-sight contact necessary
oThe major advantage of all kinds of RFID system is that they work contactlessly and require no line of sight.
Robust system
oTransponders can be read through a whole number of substances, e.g. snow, fog, ice, paint, dirt, and in difficult constructional scenarios where barcodes or other optical reading technologies would be no use at all.
Speed of an RFID system
oRFID transponders can be read at remarkable speed even in difficult conditions, and in most cases respond in less than 100 milliseconds.
Bidirectional communication
oThe reading/writing capability of an active RFID system is also a significant advantage in interactive applications, e.g. when tracking products in process or maintenance jobs.
Reliability in tough environments
oIn difficult external conditions RFID has the advantage of being able to communicate contactlessly and without direct line-of-sight contact with the data medium. Where the transponder is doesn't matter either -- it can be read through substances like dust, paint or ice.
Bulk detection
oActive and passive systems working at HF and UHF frequencies detect a number of transponders in the field. This property is called bulk capability. In practical terms it means that every data medium needn't be scanned singly, but is automatically detected during a read operation
8. COMPARISON BETWEEN RFID AND
NFC
RFID NFC
RFID uses radio frequencies for communication
NFC is a subset of RFID
RFID is capable of accepting and transmitting beyond a few meters
NFC is restricted to within 4 inches
RFID has a wide range of uses
NFC is usually used in cases where security is needed
RFID waves are either passive or active
NFC are usually passive
RFID can be used in any frequency or standard that are being used
NFC requires 13.56 MHz frequency
RFID can be used for applications like animal tracking, Vehicle tracking
NFC is appropriate for the reliable applications like mobile payments
NETWORK Low Frequency Readers WITH BIOMETRIC (THUMB) for Attendance
Features & Technical parts of Network
Biometric RFID Readers
Read and write functions.
Compact size & Wall mountable. User friendly interface. Stores Data Finger prints images Attendance record 50,000 to 1,00,000 Record Remote control & real time access & monitoring by Server Program. Authentication media : Finger print / Password / RFID card / combination.
Components of RFID Faculty Attendance System
A complete radio-frequency identification attendance system comprises of following hardware:
RF-attendance Software
RFID Readers
RFID ID Cards to faculties
Computers, Networking & UPS
Manpower for monitoring
9. METHODOLOGY
In LF – Low Frequency attendance system, low cost LF card Readers are mounted either in each class room or shared between two or more class rooms or at common entrance. Faculty shows his LF ID card to LF Reader to mark his arrival & departure.
Aim of this paper is to manage the faculty and its each and every visits from in and out of the organization. Below are the steps for controlling it.
Steps:
RFID device installed at various locations & are connected with the RFID Faculty attendance Server
housed in the campus.
When faculty enters into the organization campus, organization RFID reader reads the faculty tag and make entry in the system.
Faculty has to do thumb punching for his/her attendance as usual.
When faculty goes to take any lecture, again RFID reader in the class room reads the faculty tag and make entry in the system.
When faculty leaves the organization campus, again organization RFID reader reads the faculty tag and make entry in the system.
Data is transferred to Faculty attendance Server every 10 mins
So as and when required various management information reports should be generated to track any faculty.
Reports generated by Bio-metric system and reports generated by RFID system will be cross checked with each other to find the performance of faculty.
Depending on the cross checking, if any problem is found, management can take any corrective action to increase the faculty performance and discipline.
Need for Faculty Attendance Editing
Faculty attendance may not get marked on RFID Reader due to any one of the following Reasons.
Faculty may forget to bring the RFID ID card
His card is mal-functioning
Reader is locked
Thumb impression is not recognized by Reader
Faculty thumb / ID Card is not registered with Faculty Attendance server
Faculty may come to classes beyond stipulated time frame
Any other un-known reason
Benefits of Faculty Attendance System
Highly reliable and Real-time attendance recording for every faculty and movement tracking in and out campus.
With thumb impression, proxy attendance is zero.
It drastically reduces the faculty attendance
monitoring work of management.
It can be used as an access control system also. So only authorized persons with valid RFID card can gain access into the campus. Fully secured Campus. Integrated with Institute time table & Academic
Calendar.
Accurate and Timely Faculty Attendance
Automatic Attendance data Collection
Daily Absentee Reports to Administration & Management
Daily Attendance Register
Monthly / Yearly Attendance Reports
10. MOTIVATION
The implementation of RFID technology will definitely quickened the entire of process of recording attendance and faculty management. Manual Process of attendance taking and management of faculty will be totally removed which will save time, man power requirement and it provides very accurate output. Compared with the time consumption in auditing the faculty management, RFID technology saves considerable amount of time and greatly improves the operation efficiency. Also with the adoption of this technology the process and product quality can be improved due to reduction in punching errors by manual human operations. Labour cost is reduced to perform the value added functions.
11. CONCLUSION
The authors we have consulted in our research have shown how a system relying on RFID - technology may be developed. This system is flexible, which means that it may be extended by adding more modules. The cards that have been employed for this specific system are RFID cards, and the algorithm used has shown stable and reliable results. These cards can be put to use at the university and may replace faculty ID cards. RFID technology continues to develop, and the time has come for us to avail ourselves of its promise and convenience. The main aim of this research has been to demonstrate potential uses of RFID-technology and build a system reliant on it.
The study has identified and explained the key benefits of RFID technology. The first part of the paper explains the evolution of RFID technology and the role of its individual components within the system. The second part of the paper discusses the feasibility of employing RFID technology and how it is benefactor of improved efficiency at lowered costs. RFID technology definitely promises an increased effectiveness and improved efficiency for business processes.
References
[1] K. Domdouzis, B. Kumar, and C. Anumba, “Radio-Frequency Identification (RFID) applications: A brief introduction.”, Advanced Engineering Informatics, Vol. 21,2007
[2] S. A. Weis, S. E. Sarma, R. L. Rivest, and D. W. Engels, “Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems.” Security in Pervasive Computing, 2003.
[3] D. Zhang and A.K. Jain, “Biometric Authentication”, Proc. First International Conference on Biometric Authentication (ICBA), Hong Kong: Springer-Verlag, 2004.
[4] Intermec, “ABCs of R-9=-09090FID: Understanding and using radio frequency identification”, White Paper, (2009).
[5] Application Notes, “Introduction to RFID Technology” CAENRFID: The Art of Identification (2008).