Detecting Flooding Attacks Using Power Divergence
Full text
Figure

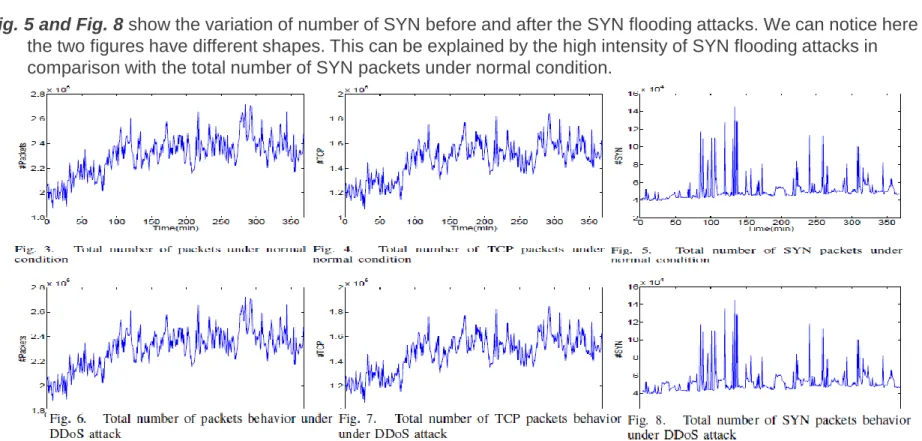
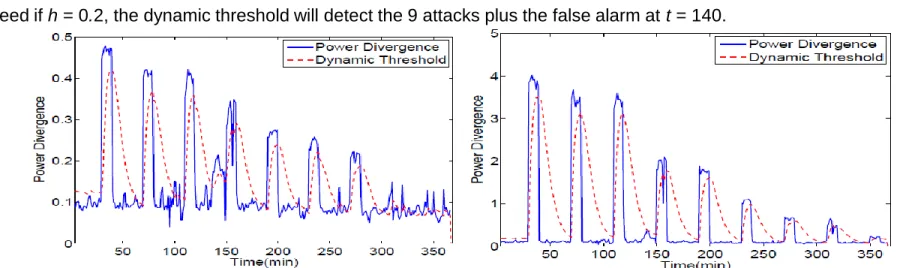
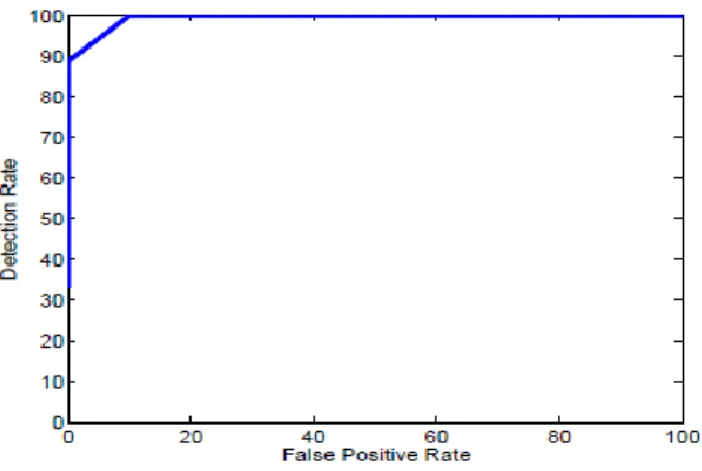
Related documents
In this thesis, we extend Hongning Wang’s work [1] of solving Latent As- pect Rating Analysis problem. We compute restaurants aspect rating by aggregating aspect rating of reviews
Unfortunately not every vertex-weighted plane triangulated graph admits a rectangular cartogram, even if we ignore the vertex weights and concentrate only on the correct
The model contains three deep neural networks (DNNs), i) a mutation encoder pre-trained using a large pan-cancer dataset (The Cancer Genome Atlas; TCGA) to abstract core
Different company departments often use dif- ferent programmed equipment that have their own data sets and the aim of the enterprise activity integra- tion is to join all
Variabel bebas dalam penelitian ini adalah rasio Kinerja keuangan , Good corporate governance dan corporate social responsibility , dan yang menjadi variabel
The einstein problem : does there exist a single tile which can only tile the plane aperiodically?.. The
The objective of this study was therefore to compare the behavior of mean velocity (MV), pacing strategy, heart rate (HR) and rating of perceived exertion (RPE) during