SECURED COMMUNICATION USING SPREAD SPECTRUM TECHNIQUES
Full text
Figure

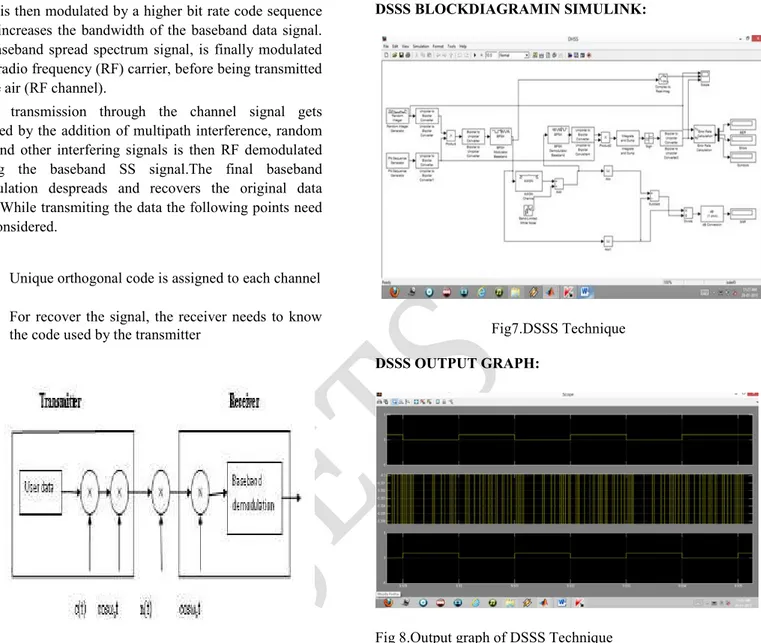
Related documents
The relative effective processing gain is used for selecting data modulation techniques that provide maximum suppression of additive interference in spread spectrum
The first science results, aimed at assessing the scientific quality of the VMC data, include an overview of the distribution of stars in colour-magnitude and colour-colour
How is bird species occurrence influenced by the size and isolation of unburnt
he analysis presented provides policy makers with an indication of those areas where individuals with a variety of health outcomes (smoking, alcohol consumption, obesity, and
In this section, we formally check if small-cap funds can be spanned by the MSCI country indices, examine the return-generating mechanism for market cap- based funds (CBFs) and
Similarly, we did not find any significant association between Snail expression and other clinico- pathologic factors (age, tumor size, grade, type of sur- gery, ALN status,
In this study, we aimed to determine the association of DSAs with primary GF, including GR and PGF, in patients who underwent unmanipulated haploidentical blood and
cyclic series, all children developed toxicity. necessitating downward revisions