Firewall Network Security
Full text
Figure
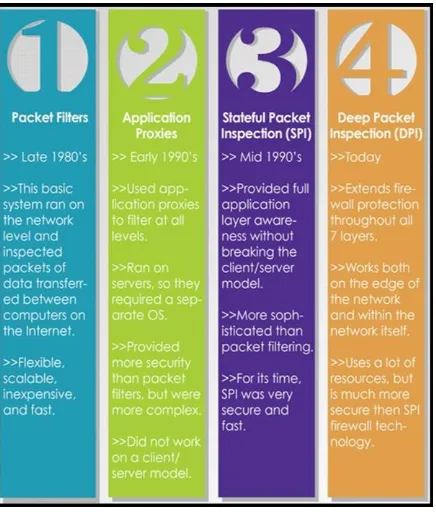

Related documents
A Monthly Double-Blind Peer Reviewed Refereed Open Access International e-Journal - Included in the International Serial Directories. of PACS and number of members has decreased
However, a definition of ideals in any additively commutative semiring S can be given which coincides with Iizuka’s definition provided that S is a hemiring, and it is called h
Wong, Best linear unbiased estimation of location and scale pa- rameters of the half-logistic distribution based on type II censored samples , Amer.. Nadarajah, Extreme
Source: National Federation of State Co-operative Bank. Table 4 shows the deposits of primary agriculture co-operative societies has increased from. Year No..
Today, one in six urban citizens in India lives below the poverty line (Ratan,2016).Despite of other challenges, ensuring basic education to every child, which is guaranteed
Then, we will explain the relations be- tween, framers and normal framers, normal framers and orthonormal basers, framers and Riesz basers, and finally, framers and the canonical
In most of the PILs that have followed over the years by the residents‟ welfare groups from middle class colonies for failure of the state to free the public spaces of
The solutions for displace- ment, temperature, stress, perturbed magnetic field in the solid consist of a dilatational wave front with attenuation depending on