Cloud Data Outsourcing and off sourcing using trust computation
Full text
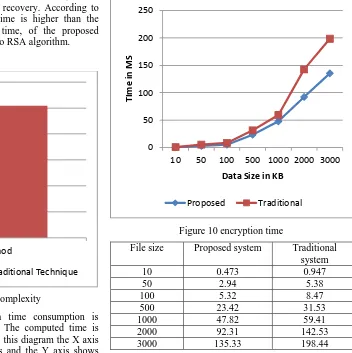
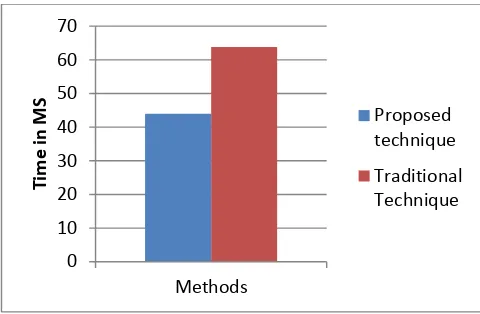
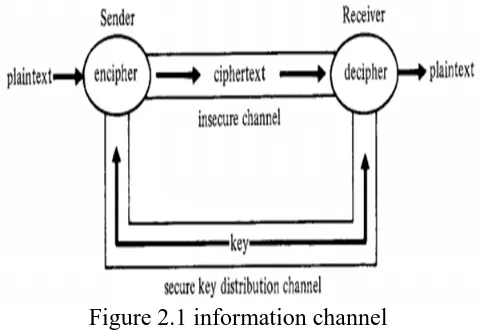
Figure



Related documents
Changing traditional range management practices and thé régulation of grazing pressure imply that control over land is taken out of the hands of the pastoralists and transferred to
In addition, both the social/personality measures (i.e., academic self-efficacy, academic locus of control, test anxiety and performance-avoidance goals) and
McKittrick – Wheelock syndrome (MKWS) was first re- ported as a rare syndrome characterized by dehydration, electrolyte depletion, and renal failure due to secretory diarrhea
BEGINNING.
With the aim of re-situating modern Iranian drama within the context of international dramatic developments, the plays of Gholamhossein Sa‘edi, Akbar Radi, and
In the following computational experiment, we applied various state-of-the-art computational models of visual attention, such as Judd model ( Judd et al., 2009 ), Erdem model (
Regions in visual cortex and posterior intraparietal sulcus (pIPS) that correlated with the graded saliency map (red) and regions in the anterior IPS and frontal eye fields (FEF)
Based on this understanding, this work focuses on the effect of the inclusion of shallow donor dopant such as gallium into the normal cadmium chloride post-growth treatment as