Implementation of Security System Using 3-Level Authentication
Full text
Figure
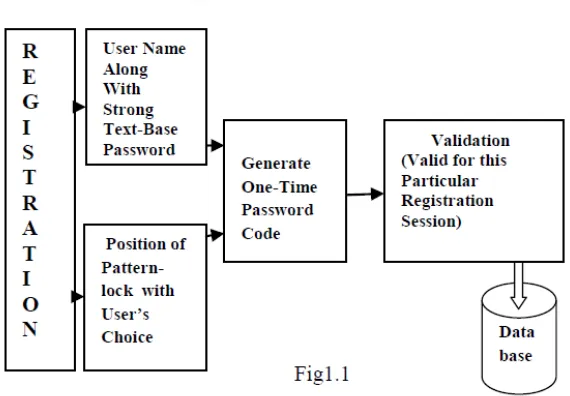

Related documents
Within forty-eight (48) hours from the proclamation of martial law or the suspension of the privilege of the writ of habeas corpus, the President shall submit a report in person or
ERBB2 amplification, germline BRCA1/2 mutations, PIK3CA mutations were classified tier of evidence IA based on large randomized trials showing antitumor activity of
sector, lacks Treasury support, and may be opposed by some emerg- ing market countries, Kenen (2002: 42) favors his own comprehensive contractual approach as “the most
As P rises, firms with lower costs enter the market before those with higher costs. Further increases in P make it worthwhile for higher-cost firms to enter the market,
The ADC, CBF and DF images were formed using the above protocols that were identied in Fig- ure 1. In the damaged areas of both the ADC and CBF maps, the values were decreased
assessment on the fresh weight counts using the Shapiro-Wilk test). The mean concentration of E. coli excreted in dairy faeces across different seasons over the
Where s is the selection coefficient for the mutational attempt, and Ne is the effective population size. We determine if the mutation was fixed by comparing
These observations show that prophylactics are not an ideal strategy in protecting youngsters against HIV and AIDS. In relation to these observations, it is argued here that