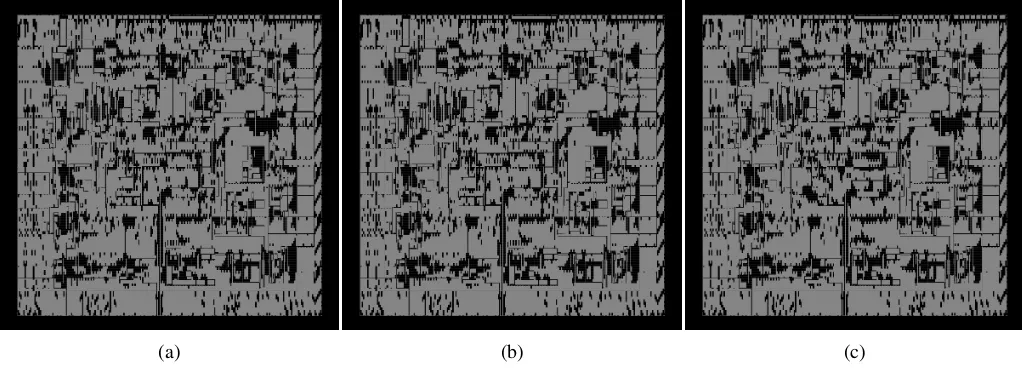
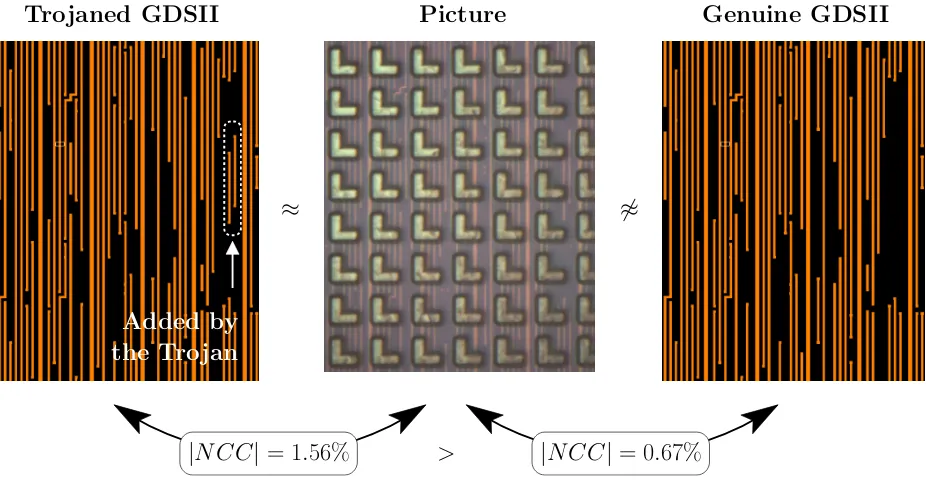
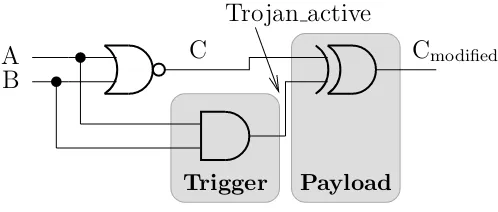
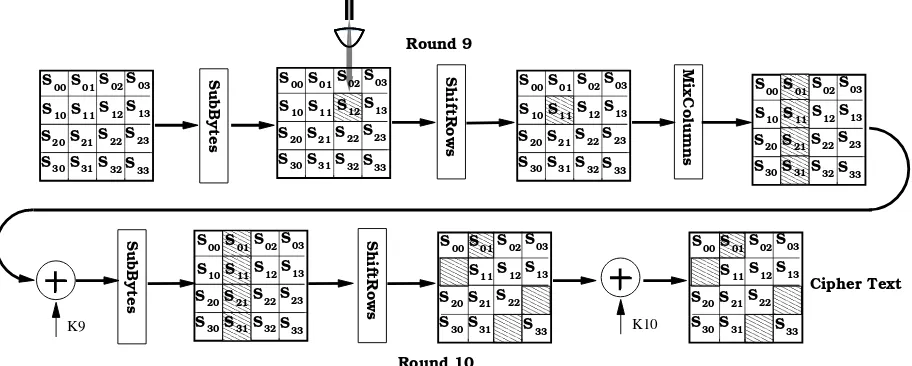
Hardware Trojan Horses in Cryptographic IP Cores
Full text
Figure
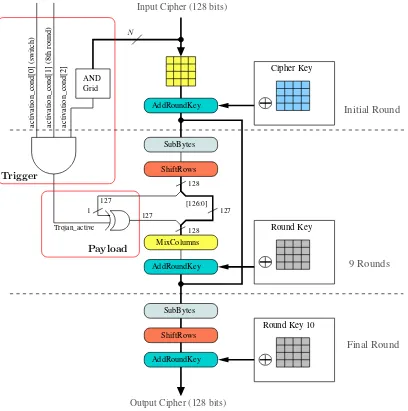

Related documents
Leading Source Code Analysis (SCA) tools provide software system architects, development managers, and individual software developers with a graphical view of the design of
When the sample containing target gas flows through the sample cell, a reduction in radiation energy is received by the detector chamber, which causes the temperature and pressure
The three-year risk-adjusted total NPV (net present value) of $161,321 represents the net cost savings and benefits attributed to using the NetApp solution when compared with
One of the technical challenges in applying our gradient computation procedure for quantum optimization problems is the need to convert between a probability oracle (which is common
Firms with a Center of Excellence in place were six times more likely to report “very successful” enterprise-wide BPM initiatives than firms with just a dedicated BPM team, and
Demersal fish landings (t) by commercial and traditional fisheries on the West Coast of Peninsular Malaysia from 1971 to 1997.. Source: Annual Fisheries Statistics 1965
To approximate the consumption of the rich, I use two approaches: one explores the data from Piketty, Saez and Zucman (2016) on the income and wealth of the rich to back out a
2013: Workshop on Behavioural and Experinmental Economics, Florence, Italy/ Summer School on “Governance and Economic Behavior,” Leuven, Belgium/ European Economic As-