A Survey Report on the Security Threats and Challenges in MANET
Full text
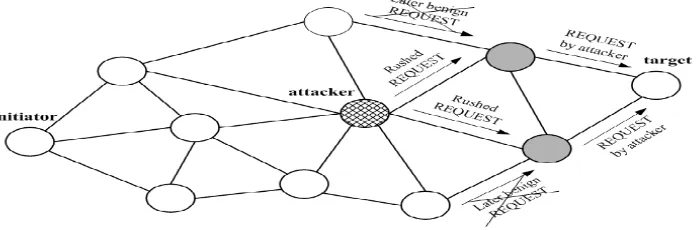
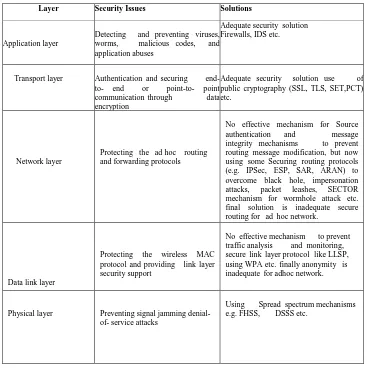
Figure
Related documents
innovation in payment systems, in particular the infrastructure used to operate payment systems, in the interests of service-users 3.. to ensure that payment systems
19% serve a county. Fourteen per cent of the centers provide service for adjoining states in addition to the states in which they are located; usually these adjoining states have
Prereq or concur: Honors standing, and English 1110 or equiv, and course work in History at the 3000 level, or permission of instructor.. Repeatable to a maximum of 6
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
Although, the present study did not find significant higher global negative expectancies for NA members relative to nonaddicted males and no significant
The total coliform count from this study range between 25cfu/100ml in Joju and too numerous to count (TNTC) in Oju-Ore, Sango, Okede and Ijamido HH water samples as
It was decided that with the presence of such significant red flag signs that she should undergo advanced imaging, in this case an MRI, that revealed an underlying malignancy, which