Security Policy Management Process within Six Sigma Framework
Full text
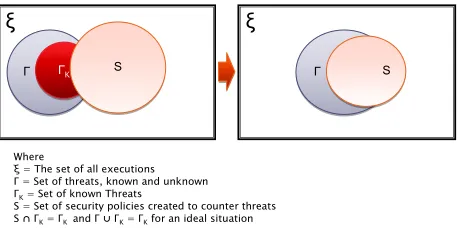
Figure



Related documents
The first stage corresponds to the loss of 33.663% of the weight of complex within the range 34-293°C corresponding to the loss of 2.5 water molecule of crystallization, two
Risk factors associated with oral candidiasis and D.S are wearing complete ( in contrast to partial) dentures, wearing a maxillary (in contrast to a mandibular)
Al-Omari, Global stability in a structured population competition model with dis- tributed maturation delay and harvesting, Nonlinear Anal., Real World Appl.. Gourley, A
The main research question is as follows: ‘ Is it feasible to design a randomised controlled trial that will assess if the Shape-up following cancer treatment programme is
Figure 4 Cognitive evolution for patients diagnosed with organic aciduria from 3 to 11 years old (A normal, B improvement, C worsening, D intellectual deficiency from the
Microbiome management in the social amoeba Dictyostelium discoideum compared to humans TIMOTHY FARINHOLT1, CHRISTOPHER DINH1,2 and ADAM KUSPA*,1,2 1Verna and Marrs McLean Department
85 International Journal in Management and Social Science http://ijmr.net.in, Email: irjmss@gmail.com Impact of microfinance on empowering women in rural area -A Study
Females were 767 and males were 250 (9 were missing).Results of this study showed that IPAQ total score was significantly correlated with WHOQOL-BREF physical, psychological

