A NOVEL ALGORITHM FOR CRYPTOGRAPHIC KEY GENERATION BASED ON SESSION AND STEGNOGRAPHY
Full text
Figure

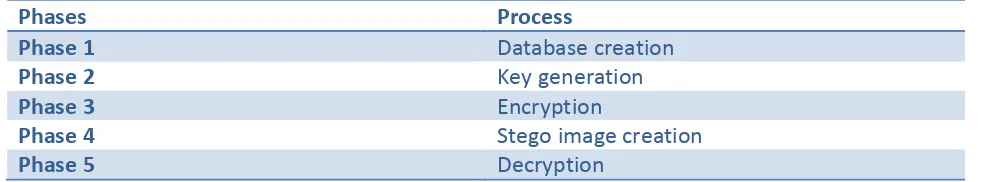
Related documents
Previous studies have considered only medical or direct expenditure while calculating the out-of-pocket expenditure on maternity care even though the indirect or non-medical costs
(Although basic math facts include addition, subtraction, multiplication, and division, this study tested multiplication only.) The students’ fluency was then related to their
UPnP Control Point (DLNA) Device Discovery HTTP Server (DLNA, Chormecast, AirPlay Photo/Video) RTSP Server (AirPlay Audio) Streaming Server.. Figure 11: Simplified
The PROMs questionnaire used in the national programme, contains several elements; the EQ-5D measure, which forms the basis for all individual procedure
We demon- strated the reduced efficacy of metrafenone to control grapevine powdery mildew in the field in 2013, as there were no differences observed in disease incidence and
An analysis of the economic contribution of the software industry examined the effect of software activity on the Lebanese economy by measuring it in terms of output and value
The analysis of the given definitions allows to come to a conclusion that the trust in its classical understanding is the transfer of the property by
Just as your friendly smile and attitude welcomed the guest into the Wurst Haus German Deli & Restaurant, your pleasant farewell leaves the guest feeling good and wanting