CRYPTOSCANF: CRYPTOSYSTEM USING CFG
Full text
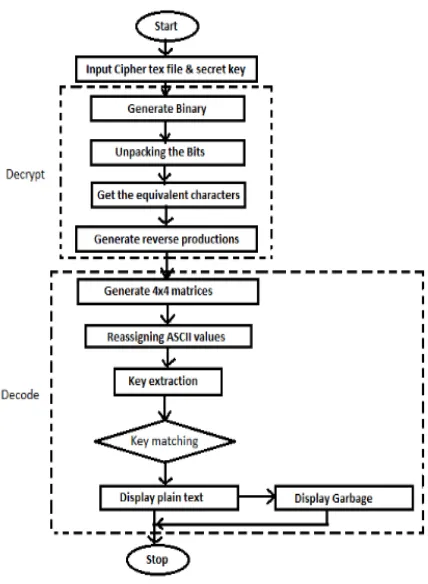
Figure

Related documents
For a teacher to say that a book, poem, play, or short story has literary merit and deserves to be taught in a classroom, they might look at themes of the text, the time period, use
agrees to risk some material possession to other players in!. exchange for the chance to win the possessions of
Based on the findings of the survey, it is recommended that the private sector should adopt the following health care measures for the employers: conduct health audit of all
In summary, we name this autosomal dominant condition ROSAH syndrome to reflect the most common features across affected individuals: retinopathy, optic nerve edema, spleno-
I Given an ambiguous grammar for expressions, construct an equivalent unambiguous grammar (given associativity and precedence rules). I Typical kinds of unambiguous grammars that
Gray, the Board voted, 4-0, and the motion carried to approve the minutes for the regular session and the Executive Session verification on February 21, 2012 as
This week, Life Training Online will be reviewing Ask and It Is Given: Learning to Manifest Your Desires, by Esther and Jerry Hicks, the fourth of fifty-two books in the 52
Hands with an ss consultancy consumer complaints and insurance companies offer those who are no longer available placement consultancy for candidates in your complaint to