Keystroke Dynamics Based Authentication As A Service
Full text
Figure
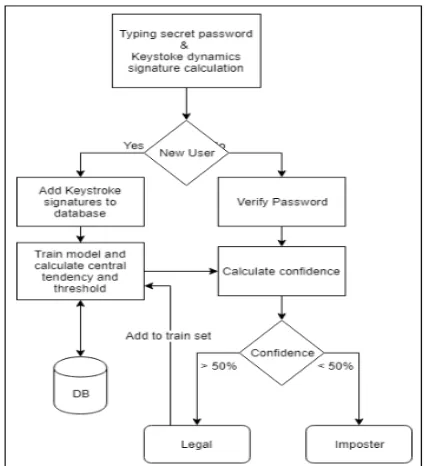
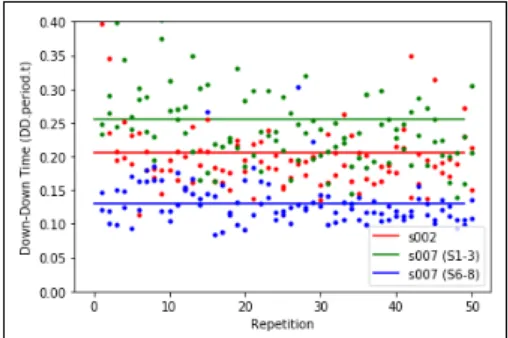
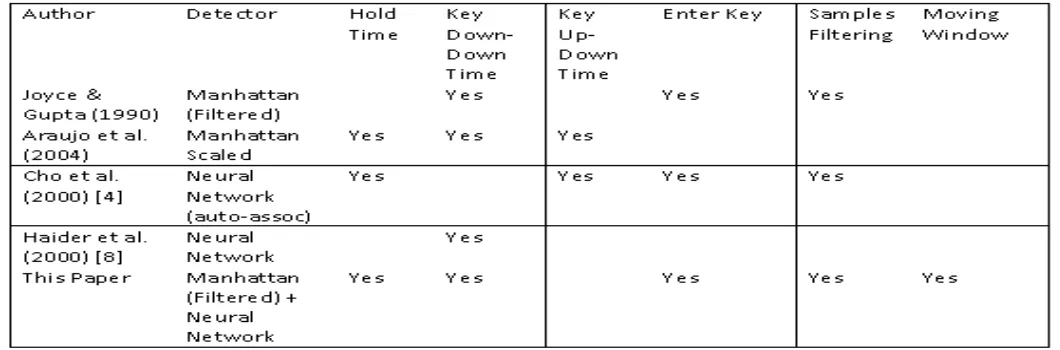
Related documents
Water service to more than 4,000 LaBarr Meadows, Alta Sierra, and Brewer BEP area connections rely on a single water main to and from Osborn Hill Tanks as a source of supply..
Bayesian model selection for time series using Markov chain Monte Carlo. A reversible jump sampler for autoregressive time series, employ- ing full conditionals to achieve
Of particular interest are the coal-fired thermal generation units that are operated under the terms and conditions of the Power Purchase Arrangements (PPAs). Outages at these
Evolution ™ Series Switchboards...12-2 Spectra ™ Series Switchboards ...12-5 Commercial Metering Switchboards...12-8 Spectra ™ Integrated Switchboard Solutions ...12-11 GE
Both ‘instrumental variables’ lead to the same conclusion: from 1970 to 1990 immigration caused a positive ‘productivity effect’ on natives in US cities, associated with higher
Children and adolescents who are involved in bullying others and who are also being bullied by others are at the greatest risk for negative mental and physical health
Eight of these species—the water snake, brown snake, redbelly snake, eastern garter snake, ribbon snake, ringneck snake, smooth green snake, and milk snake— occur statewide.. Of
Keywords: Multiple Model, Prediction of Internet End-to-End Delay, Joint Decision and Estimation, Joint Tracking and Classification, Surveillance Testbed, Wireless Sensor Network...