Security issues of Power line Communications
Full text
Figure
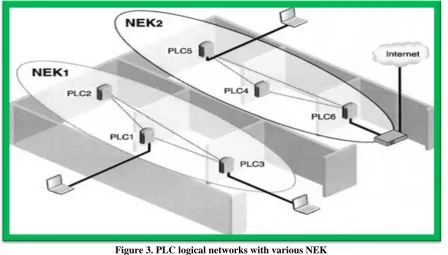

Related documents
categories are as follows: certification exemptions, accepted practices for small composting facilities, medium scale categorical composting facility certifications, large
As MIT began posting its first open courses at the forefront of the OCW movement, there was the hope that the open knowledge and pedagogical wealth created
Section 10A (b)(2), “Response to Failure to Take Remedial Action,” requires that the independent auditor, as soon as practicable, shall directly report to the board of directors
A num ber of ot her m echanism s such as spat ial segr egat ion, polit ical econom y, public opinion and shift s in social and cult ur al nor m s have been explor ed in a r elat
The revised fact sheets includes information about the report of the National Academy of Sciences’ Institute of Medicine on Agent Orange and Type 2 diabetes, VA’s decision to
This method has four step – plan (planning the intended improvement), do (implementation of plan), check (verification of the result of the implementation compared to the
The four major investor-owned utility members of ERCOT are American Electric Power (which recently purchased Central and Southwest), Southwestern Electric Service Company,