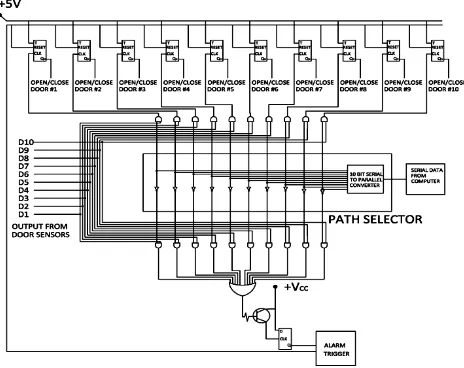
Design and Implementation of an Open Ended Automated Vault Security System
Full text
Figure




Related documents
In the event that the Storage User decides to transfer any amount of the booked storage capacity to fixed storage capacity (hereinafter referred to as Fixed
According to the results obtained from experiment and model for several samples with different characteristics, it could be observed that by increasing the fiber
Having separated the liquids and solids wastes component, TCLP results.. showed higher concentration of toxic contaminants such as Arsenic, Barium,
First review stage: Statements and documentation to warden: Note that the BOP will require not only statements laying out the reasons for the request, but also
in area of crime control, criminology and criminal justice closely merge criminal justice academic education and training.. similarities between
Also, position and research papers pertaining to mental health programs for low income groups, collective bargaining issues relating to job security for mentally ill workers,
It is based on the aforementioned, that this study investigated the extent to which leadership styles (transformational, transactional and laissez-faire) relate
For this study, data from the referring hospital was extracted from the ICU admission and discharge register, and patients’ folders, while data during transfer