Pixel Value Graphical Password Scheme: Compatibility of K-means Clustering Algorithm as Pixel Value Password Fault Tolerance Mechanism
Full text
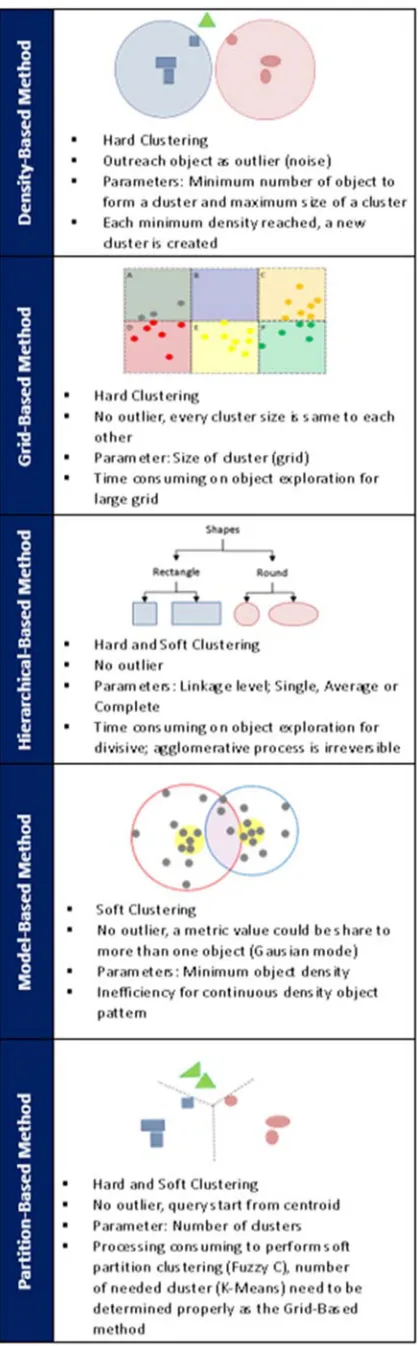
Figure



Related documents
The dotted line is a linear fit to the data indicates a possible relationship between the magnitude of the isotope shift, ∆T c ,and the width of the transition. In
We invite unpublished novel, original, empirical and high quality research work pertaining to recent developments & practices in the area of Computer, Business, Finance,
WENNER ~ MUSICK (1974) demonstrated that silver males had larger eyes relative to gape length than females and that silver female eyes were slightly larger than
Nonetheless, having finally completed all the myriad necessary arrangements I now had to quickly shift focus to facilitate actually shooting the film which was still, even at
Jolly acqua fredda-temperatura ambiente-frizzante a secco con pompa rotativa Jolly overcounter cooler for cold-ambient-carbonated water dry cooling with rotary pump
Besides, It has been observed by researchers [1], [2], [15] that many conventional supervised learning problem- s, such as multiclass classification and multilabel classification,
The bond shall not be released until an engineer certification and as built plan is submitted certifying that the drainage and road remediation is complete and all building