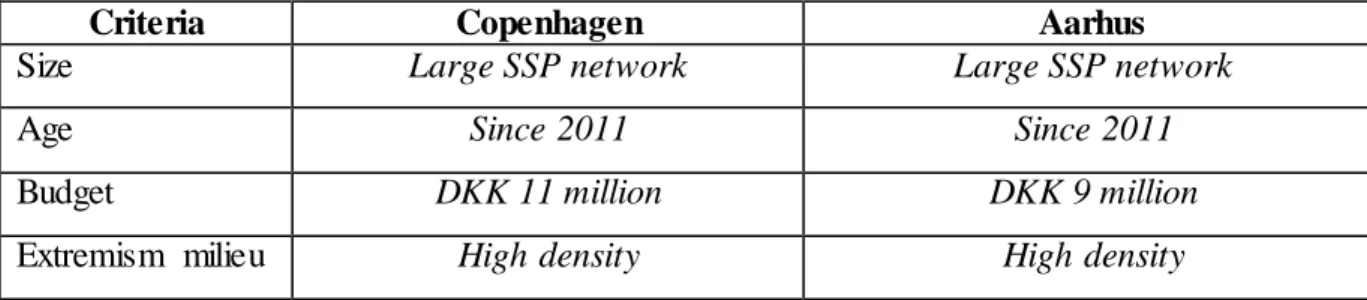
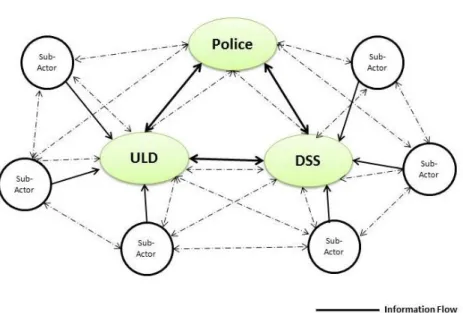
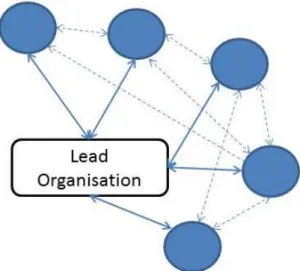
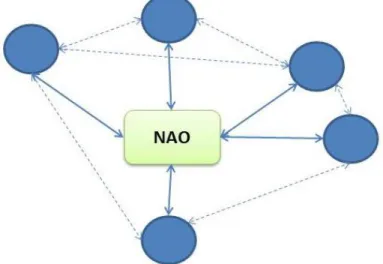
Local Security Networks: Structure and Counter-radicalisation Output
Full text
Figure


Related documents
The aim here was to investigate the risk of recurrence of CIN II/III among HIV-infected women (HIV+) and uninfected women in a cohort treated by means of large-loop excision of
In deze thesis is er voor gekozen om onderzoek te doen naar mensen met een verstandelijke beperking omdat deze groep vergeleken met andere WMO doelgroepen weinig mogelijkheden
We find that due to network externalities, prices for both products in the closed source model and for the complementary product in the open source model will begin low in order
These errors occurred because (1) State agency instructions on the hospital incentive payment and patient-volume calculations were incorrect or lacked needed information, (2)
Any financial institution – be it a securities firm, an insurance company, a hedge fund, a private equity firm, or a bank holding company – which is not now subject to the
As discussed in the previous sections, the suitability of transactional databases, operational data stores, data warehouses, and virtual databases depends on
NOMINAL PURPOSE: DISCUSSION OF TESTS FOR ACCURACY AND RESIDUALS, OPTICAL EFFECTS FOR EACH CLOUD FLAG, INTEGRATION WITH OTHER PRODUCTS, 3-D CLOUDS, AND SHADOWS..